Understanding the Levels of Cyber Threat Intelligence
Aug 12, 2023
The model for cyber threat intelligence levels can vary across different organizations and industries, so there isn’t a universally standardized model. Traditionally, the three-level model consisting of tactical, operational, and strategic threat intelligence has been more widely adopted.
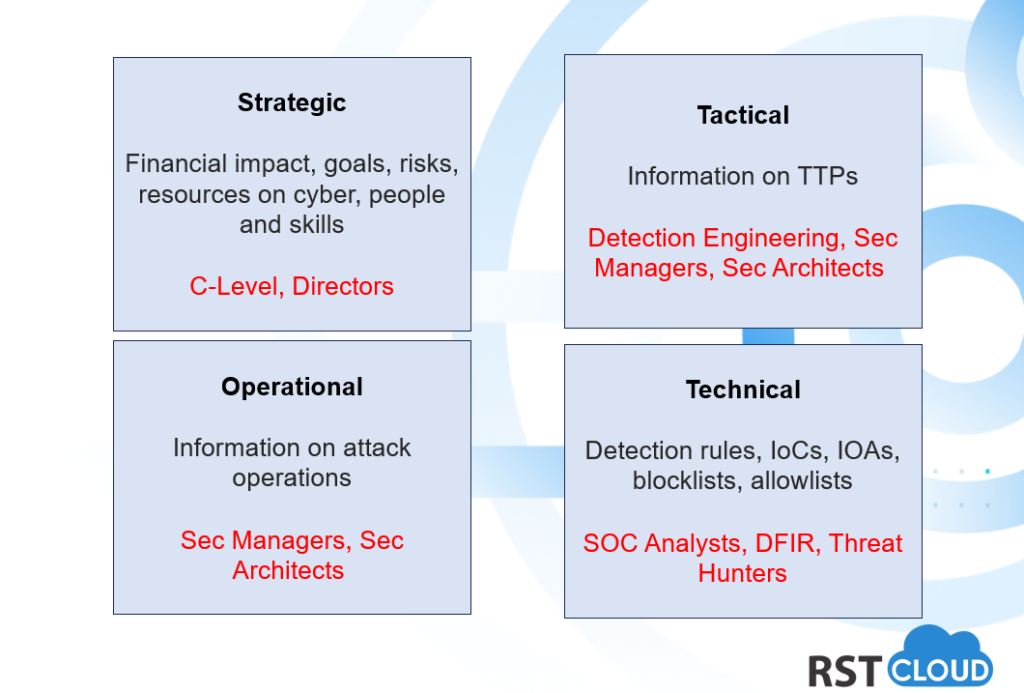
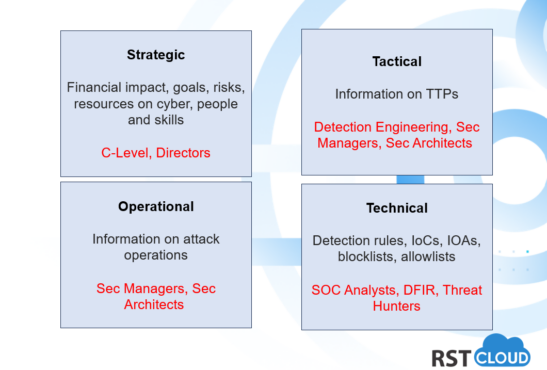
Another popular model has four levels. The latter model includes technical threat intelligence and expands on the traditional model by incorporating a more granular level focused on technical aspects. Technical Threat Intelligence focuses on practical details and analysis, such as reverse engineering malware, network forensics, and vulnerability research.
- Strategic Threat Intelligence: Shaping Organizational Strategy
Strategic threat intelligence provides a panoramic view of an organization’s threat landscape. Tailored for executive-level security professionals (CISO, CSO, CTO, CEO), it presents findings to help to decide on cyber goals for the organization, allocate enough resources and budget, select what should be a top priority, what people and skills are required for the team based on the risks the organization is facing. The goal is to empower decision-makers to steer the organization’s overarching strategy in response to the identified threats. This form of intelligence focuses on the broader trends and potential risks that could impact the business’s core operations and reputation.
- Operational Threat Intelligence: Deep Insights into Attack Operations
This level focuses on the broader context of threats. Operational threat intelligence hones in on the operational aspects of attacks and behavior of attackers. It provides comprehensive insights into factors such as the nature, motive, timing, and execution methods of attacks. This type of intelligence often involves gathering information from hacker chat rooms and discussions online, often through infiltration. Due to its clandestine nature, obtaining operational intelligence can be challenging but immensely valuable.
- Tactical Threat Intelligence: Unveiling Threat Actors and Techniques
This level focuses on immediate threats and provides actionable information for security operations. Moving from the higher levels to the security team, tactical threat intelligence offers a more detailed perspective. It dives into specific details about threat actors, their tactics, techniques, and procedures (TTP). This intelligence helps security professionals understand the potential attack vectors, enabling them to build robust security strategies against these threats. By delving into the specifics of how attacks are carried out, the security team can take proactive measures to mitigate potential damages.
- Technical Threat Intelligence: Clues and Evidence for Analysis
Technical threat intelligence takes a more hands-on approach. It focuses on specific indicators of compromise (IoCs) or indicators of attacks (IoA) – the signs of an ongoing, historical, or potential attack. Security operations specialists scan for these IoCs and use them as the foundation for detection and understanding of attacks. It encompasses the examination of malware, vulnerabilities, exploit techniques, infrastructure details, and digital forensics data. This type of intelligence is geared towards cybersecurity professionals responsible for configuring, maintaining, and defending technical systems. The aim of technical TI is to provide actionable insights that enable these professionals to prevent attacks, proactively mitigate vulnerabilities, and respond effectively to emerging threats at the technical level.
Whether the three-level or four-level cyber threat intelligence model makes more sense depends on the specific needs and context of an organization. Some organizations may find the additional granularity of technical threat intelligence valuable, while others may prefer a more streamlined approach.
Ultimately, it’s essential to tailor the threat intelligence model to the specific requirements and objectives of the organization. The model should align with the organization’s risk appetite, available resources, and the nature of the threats they face.