Get global threat intelligence context from RST Cloud
Our mission is to provide SecOps teams with high-quality Cyber Threat Intelligence, democratise and revolutionise the field of CTI, and make it accessible, affordable, and effective for a wider range of companies across the globe. Ultimately, we aim to contribute to a safer and more secure digital landscape for all.
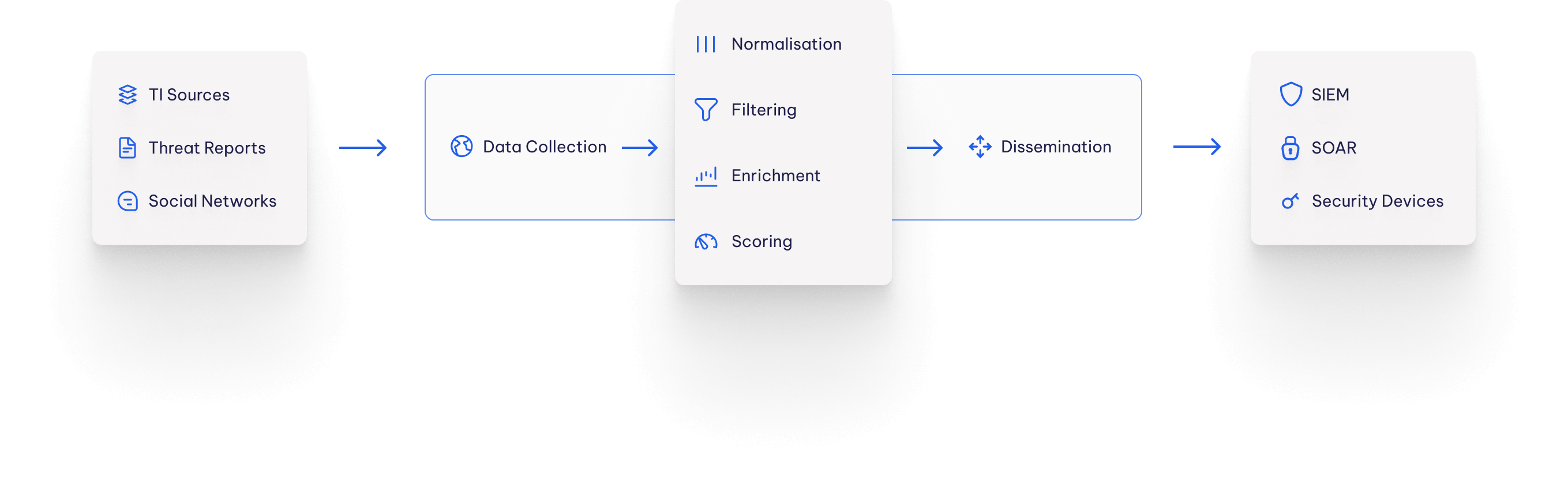
RST Cloud Engine
Integration
We provide quick and easy out-of-the-box integration with many SIEM, SOAR, TIP, EDR, XDR, NGFW, and WAF solutions. The knowledge we produce is actionable to the extent that machines can facilitate end-to-end detection, prevention, and response.
Fortigate firewalls can directly be integrated with RST Threat Feed via API. It gives options to block or alert on access to malicious websites or IP addresses. The integration is seamless and requires no extra software to be used to configure the firewalls.
Palo Alto NGFW can directly be integrated with RST Threat Feed via API. It gives options to block or alert on access to malicious websites or IP addresses. The integration is seamless and requires no extra software to be used to configure the firewalls.
RST Thread Feed integrated with IBM Qradar SIEM via RST Downloder agent. This agent automatically downloads all the required data and pushes it to the SIEM via API. There are options to filter indicators through its score and types, malware, tags etc
Palo Alto Cortex XSOAR can directly be integrated with RST Threat Feed via API. It gives an ability to query RST Cloud API directly from any playbook or using the war room commands.
RST Thread Feed integrated with Splunk. The app is published on the official Splunk marketplace and allows to automate downloading and maintenance of the feeds into Splunk.
RST Thread Feed is integrated with Microsoft Sentinel SIEM via a standard STIX/TAXII integration. There are options to filter indicators through its score and types, malware, tags etc
RST Thread Feed is integrated with Elastic SIEM solution via a custom elastic filebeat/agent configuration. There are options to filter indicators through its score and types, malware, tags etc
RST Thread Feed is integrated with MISP via a python script. There are options to filter indicators through its score and types, malware, tags etc
Cisco Firepower can directly be integrated with RST Threat Feed via API. It gives options to block or alert on access to malicious websites or IP addresses. The integration is seamless and requires no extra software to be used to configure the firewalls.
SAF Systems is a versatile platform for collecting and analysing machine data. It works in the fields of information security, IT infrastructure monitoring, and business process analysis. The integration of RST Threat Feed and RST Report Hub within the SAF platform empowers analysts to make informed decisions.
Enrichment
Many threat intelligence data come with little or no context, making it challenging for cybersecurity professionals to determine the appropriate course of action. This can lead to extra work as they try to assess the risk level of indicators of compromise (IoCs) and decide whether to action them or further investigate potential threats.
After aggregating indicators of compromise such as IP addresses, domain names, and file hashes from multiple sources, we add valuable context to help cybersecurity professionals more effectively assess the threat level of indicators. Our enrichment process adds the following context to indicators:
- Threat category (e.g. phishing, malware, ransomware)
- Malware family (e.g. Emotet, Trickbot, Ryuk)
- Common Vulnerabilities and Exposures (CVE)
- Attribution to Threat actors (e.g. APT groups, cybercrime organisations)
We use a combination of external sources and our own proprietary methods (such as RST Honeypot Network, RST C2 Tracker) to consistently and reliably add this context to indicators. This helps cybersecurity professionals more effectively assess the threat level of indicators and decide on appropriate courses of action quicker.
After threat data is aggregated from multiple sources we contextualise it by adding:

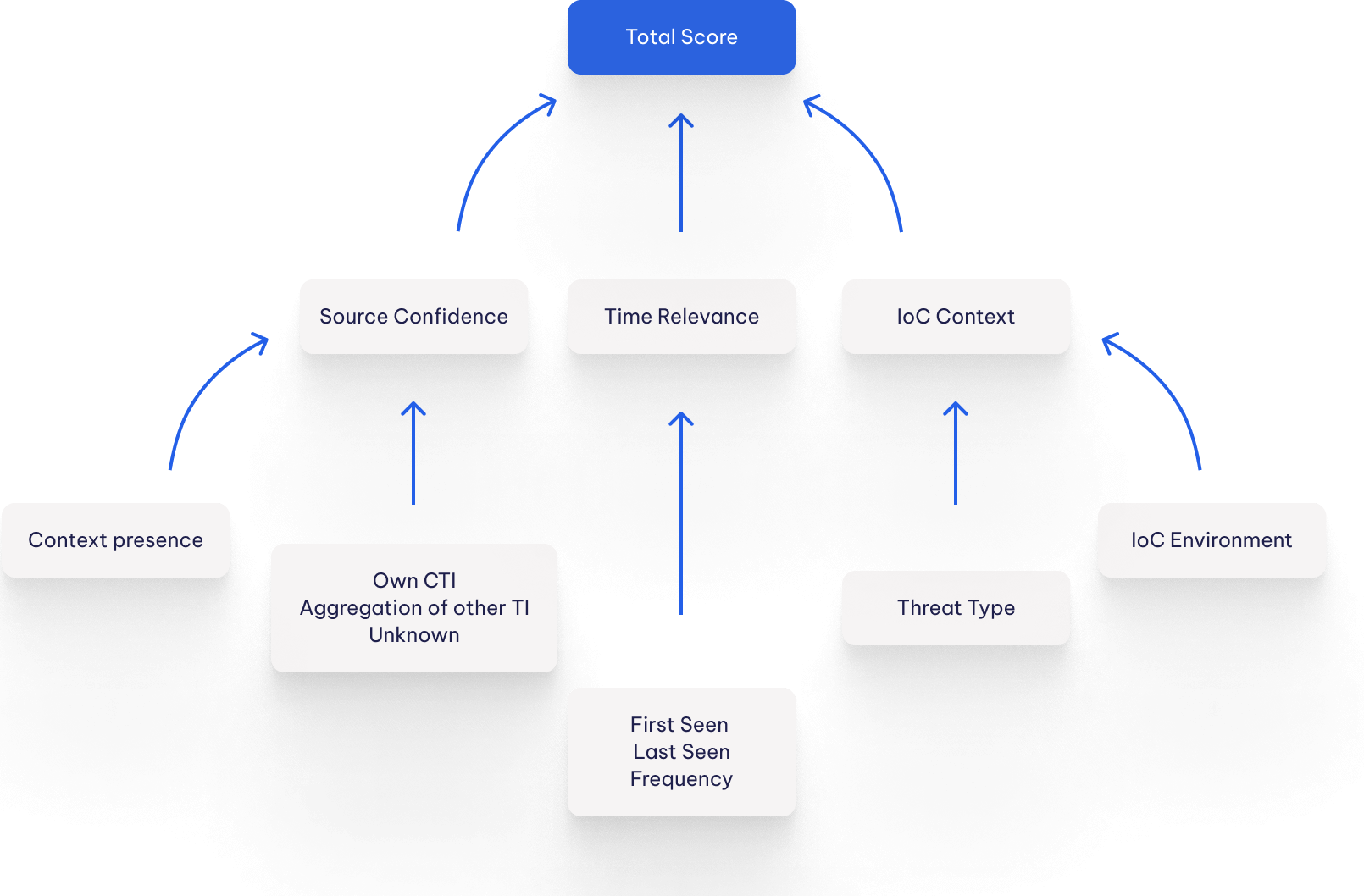
Scoring
Cybersecurity professionals often face a deluge of alerts on a daily basis, as hundreds of threats target organizations that rely on the internet for their daily operations. To help prioritize these alerts and focus on the most critical ones first, we use algorithms to rank every indicator with an appropriate score.
Our scoring process helps you identify the indicators that are most likely to pose a threat and should be investigated first. By sorting alerts by score, you can quickly focus on the most relevant and actionable pieces of information, helping you to streamline your workflow and more effectively protect your organisation against cyber threats.
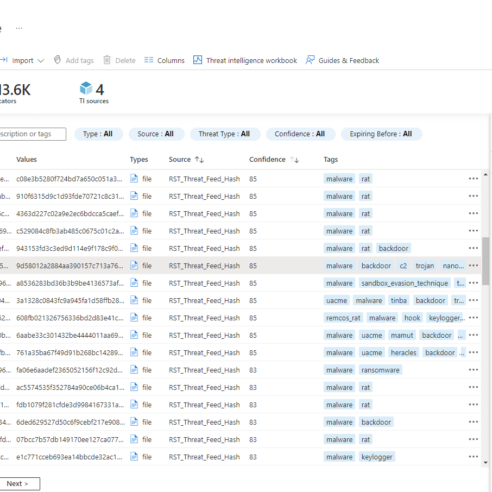
RST Threat Feed is a subscription-based service that delivers indicators of compromise collected, aggregated, filtered, and scored from hundreds of threat intelligence sources. Our solution enriches indicators with comprehensive context to accelerate incident prevention and response and enables automation solutions with actionable data.
Explore our extensive electronic library housing threat reports from various security companies, independent researchers, and communities. These reports are meticulously transformed from human-readable formats into machine-readable formats, including STIX 2.1. Gain access to valuable insights to bolster your cybersecurity strategy and stay informed about emerging threats.
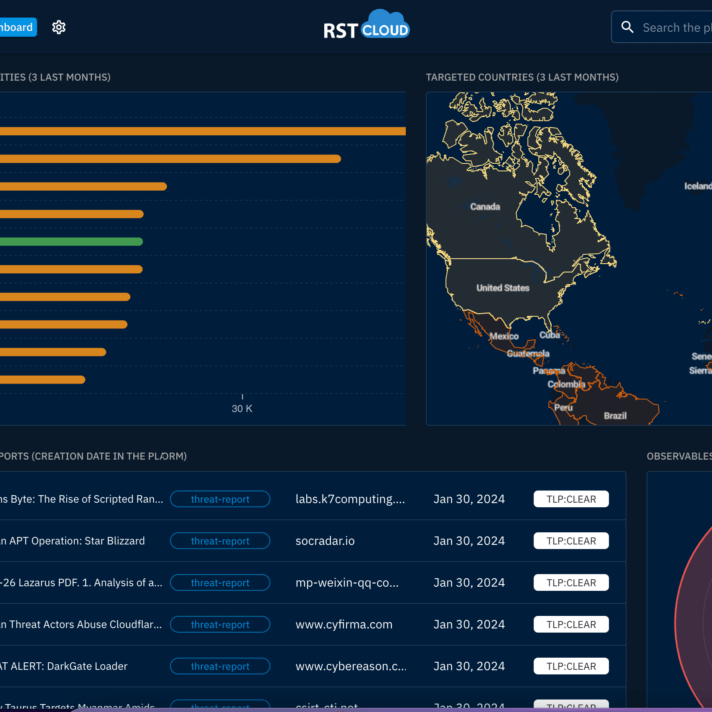
Enrichment services for SOC teams
The RST Noise Control API enables users to verify whether an indicator or a batch of indicators are deemed "known-good" and therefore classified as noise. With the RST IoC Lookup API, users can check individual values to determine if they are suspicious or malicious indicators, including IP addresses, domains, URLs, and hashes (MD5, SHA1, SHA256). Additionally, the RST Whois API provides registration information in JSON format, offering unlimited speed and no risk of being banned from WHOIS servers. This data can provide valuable information for recognising phishing or fraudulent resources.
{
"status": "registered",
"registered?": "true",
"created_on": "2022-01-01 00:00:00",
"updated_on": "2022-01-01 00:00:00",
"expires_on": "2023-01-01 00:00:00",
"age": 365,
"registrar": "Registrar Name",
"registrant": "Registrant Name",
"nameservers": "ns1.domain.com,ns2.domain.com"
}
Get Free Trial
Choose a product and get your trial account by email. By signing up for a free trial, you grant RST Cloud permission to contact you via the provided email address for purposes related to your trial, account management, and relevant product information.