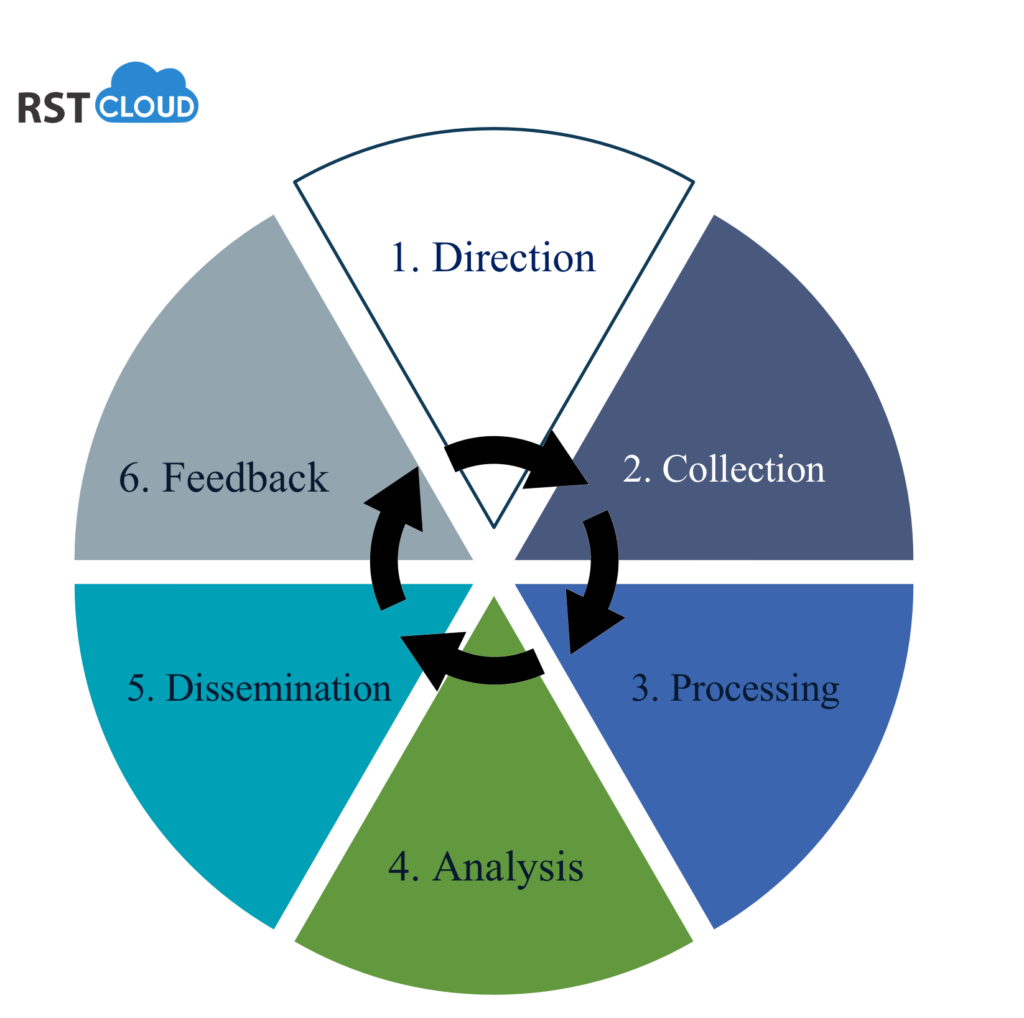
The Six Phases of Developing an Effective Threat Intelligence Lifecycle
Sep 8, 2023
In today’s cybersecurity landscape, staying ahead of threats requires a structured and methodical approach. The threat intelligence lifecycle comprises phases that organizations must navigate to develop a successful and robust security strategy. Let’s break down the six key phases:
1. Direction: Defining Objectives and Goals
During this initial phase, the developer defines the goals of the threat intelligence application. This involves identifying critical business assets and processes that require protection. By evaluating the potential impact of asset loss or process interruption, the organization can determine the specific threat intelligence needed. This phase lays the groundwork for formulating essential questions that the program will eventually answer.
2. Collection: Gathering Necessary Information
In the collection phase, the focus is on accumulating the necessary information to address significant intelligence requirements. Data can be sourced from various channels, including extracting logs and metadata from security devices and internal networks, subscribing to multiple threat data feeds, and engaging with knowledgeable sources. This phase addresses questions related to potential blind spots, collection techniques, and the feasibility of infiltrating closed sources on the Dark Web.
3. Processing: Turning Raw Data into Usable Information
In the Processing phase, the raw data collected is transformed into a format that is easily consumable by stakeholders across the organization. This transformation can be accomplished through manual or automated processes, converting raw data into structured and usable information.
4. Analysis: Translating Data into Actionable Intelligence
The Analysis phase is where processed data takes on a new dimension – actionable intelligence. This intelligence informs various decision-making processes, such as investigating potential threats, taking proactive measures to counter ongoing attacks, enriching threat intelligence with more meaningful data, and reinforcing security controls. Effective presentation of analysis results is crucial, ensuring that decision-makers can comprehend and act upon the information efficiently.
5. Dissemination: Sharing Insights
The Dissemination phase involves distributing the insights gathered, processed, and analyzed to the relevant teams within the organization. Effective dissemination ensures that the right stakeholders receive threat intelligence data that align with their responsibilities and roles, empowering them to make informed decisions and take appropriate actions.
6. Feedback: Continuous Improvement
The final phase of the threat intelligence lifecycle is Feedback. Organizations seek input from various teams utilizing the threat intelligence to continuously refine its accuracy and relevance. Different teams have distinct functions and rely on specific data points. This iterative feedback loop enhances the overall effectiveness of threat intelligence and ensures its continued alignment with organizational needs.
In Conclusion
In the ever-evolving world of cybersecurity, threat intelligence serves as a guiding light, illuminating potential paths that threats may take. Strategic, tactical, operational, and technical intelligence collectively form a comprehensive shield against cyber adversaries. By meticulously following the six phases of threat intelligence development, organizations can remain prepared, proactive, and resilient in the face of evolving threats.
Understanding the nuances of each phase and how they interconnect is key to developing a robust and effective threat intelligence strategy that safeguards digital assets. The threat intelligence lifecycle is not a linear process but a continuous cycle that adapts and evolves to stay ahead of cyber adversaries and protect organizations from emerging threats.