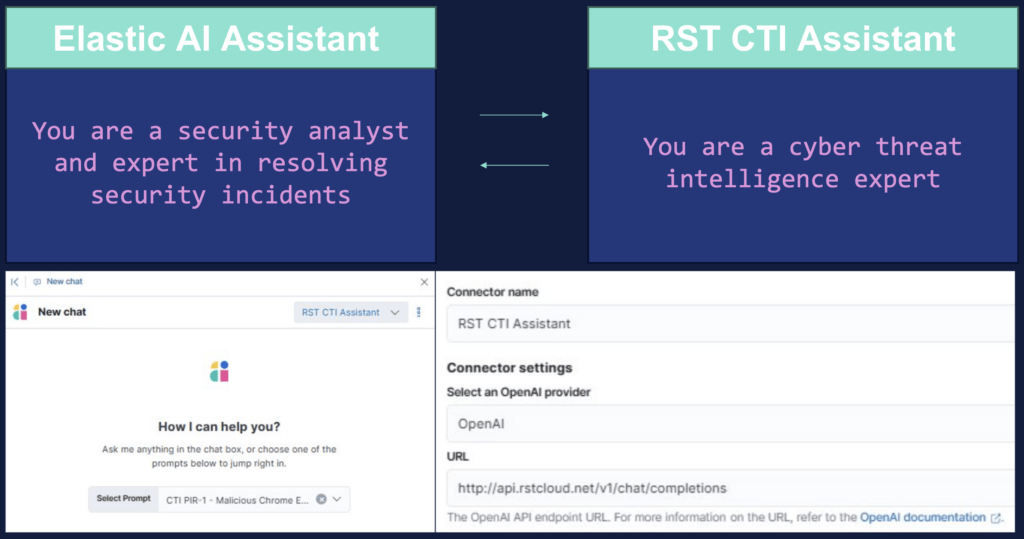
Your Threat Hunters Are Spending Their Day Reading Blogs. Here’s How to Fix That.
By Yury Sergeev and Juanita Koschier, RST Cloud Picture your best threat hunter. They came up through incident response, they think like an adversary, and they know your environment better than anyone. Now picture what they actually spent the first two hours of their day doing: reading threat reports, skimming vendor blogs, manually checking whether any of it is […]
Your Threat Hunters Are Spending Their Day Reading Blogs. Here’s How to Fix That. Read More »