RST Threat Feed with Sophos Firewall
Integrating RST Threat Feed with Sophos Firewall empowers organisations with real-time threat intelligence to detect and block evolving cyber threats effectively. Our feed provides comprehensive coverage across various threat categories, including phishing, ransomware, stealers, web attacks, command and control (C2) servers, botnets, malware, and more. By leveraging indicators such as IPs, domains, and URLs, Sophos Firewall users can enhance their network security posture and proactively mitigate threats.
RST Cloud aggregates threat intelligence from a wide range of sources, including private and open feeds, in-house analysis, public sandboxes, C2 Tracker, and our global Honeypot Networks, ensuring up-to-date and actionable data.
Prerequisites:
- Sophos Firewall version 21 or higher
- Credentials for RST Threat Feed for Sophos NGFW, which you can request via our contact form or by emailing info@rstcloud.net
Configuration Steps
The feature named "Third-party threat feeds" allow you to add threat intelligence from external threat feed sources to the firewall.
1. Navigate to the “Active Threat Response”section in the Sophos Firewall admin console.
2. Locate “Third-party threat feeds”and click “Add” to configure a new feed.
Enter the following details:
Name: Example "RSTTF-url-c2" (can be any custom name).
Description: Add relevant feed details.
Action: Choose either Monitor or Block depending on your security policy.
Position: Select Top or Bottom to prioritise the feed.
IoC Type: Create separate feeds for IP, domain, and URL indicators.
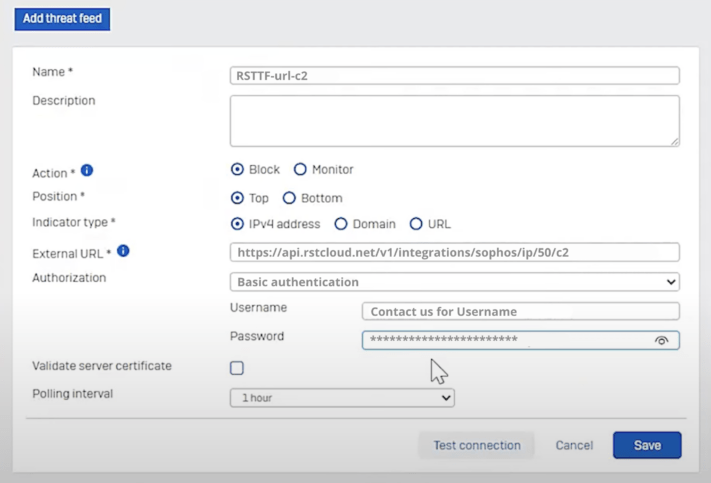
4. Input the External URL provided by RST Cloud:
For Internal -> External Blocklists:
GET https://[username]:[password]@api.rstcloud.net/v1/integrations/sophos/[indicator_type]/[score]/[category],
indicator_type (mandatory): ip, ip_src, domain, url
score (mandatory): from 0 to 100
category (optional, requires score to be specified): all, backdoor, badbot, banker, bootkit, botnet, c2, clicker, cryptomining, ddos, dns, downloader, drainer, dropper, fraud, generic, keylogger, malware, phishing, proxy, raas, ransomware, rat, rootkit, scam, scan, screenshotter, shellprobe, spam, spyware, stealer, tor_exit, trojan, vpn, vulndriver, webattack, wiper
Example of Internal -> External Blocklists requests:
- https://api.rstcloud.net/v1/integrations/sophos/ip/50/c2
- https://api.rstcloud.net/v1/integrations/sophos/domain/50
- https://api.rstcloud.net/v1/integrations/sophos/url/50
Example of External -> Internal Blocklists requests:
- https://api.rstcloud.net/v1/integrations/sophos/ip_src/60
5. Under Authorisation, select Basic, and obtain credentials by contacting us at trial@rstcloud.net or via our contact form.
6. Set the Polling Interval to 1 hour for timely updates.
Once configured, detected threats will appear in the Sophos Firewall logs with the label you assigned under the “Threat” field.
By integrating RST Cloud with Sophos Firewall, organisations gain a proactive approach to network security, ensuring robust defence against emerging threats and minimising risks across their digital environments.