Featured integrations
The knowledge we produce is actionable to the extent that machines can facilitate end-to-end detection, prevention, and response, relying on data sourced from RST Cloud
Unlock Advanced Threat Intelligence Capabilities with RST Cloud's Seamless Integration with OpenCTI
Empower your threat intelligence workflow by leveraging the seamless integration of OpenCTI with the RST Threat Feed, RST Report Hub, and RST Noise Control. This connector delivers our daily feed of IP, Domain, URL, and Hash indicators directly into OpenCTI, enhancing your organization's ability to stay ahead of emerging threats.
Enriched with valuable context, including malware names, CVE details, threat actor information, TTPs (Tactics, Techniques, and Procedures), scoring, and more, the RST Threat Feed connector streamlines and fortifies your threat intelligence capabilities.
To complement this integration, the RST Report Hub connector seamlessly integrates a diverse range of APT reports. These reports, sourced from security companies, research groups, cyber communities, and individuals, are directly integrated into your OpenCTI environment.
Ensure quality of the incoming data from various threat intelligence sources by checking indicators and observables automatically using RST Noise Control connector. This ensures that well-known and benign IPs, Domains, URLs, and Hashes will not trigger False Positive alerts after data has been disseminated to other security tools.
Key Benefits:
- Easy curation of CTI data: map indicators to threat actors, malware, vulnerabilities, tools and other objects
- Effortless STIX Graph Creation: Easily create a STIX graph from a report, simplifying threat intelligence analysis.
- MITRE ATT&CK® Mapping: Develop a MITRE map for a threat actor, providing comprehensive insights into their tactics.
- APT Report Compilation: Compile a list of ingested APT reports for comprehensive threat intelligence gathering.
- Indicator List Generation: Gather indicator lists with ease, enhancing your organization's proactive security measures.
Experience the synergy of OpenCTI and RST Cloud, and elevate your organisation's ability to effectively combat cyber threats.
RST Threat Feed for OpenCTI is available on the GitHub and can be easily installed and configured by OpenCTI users.

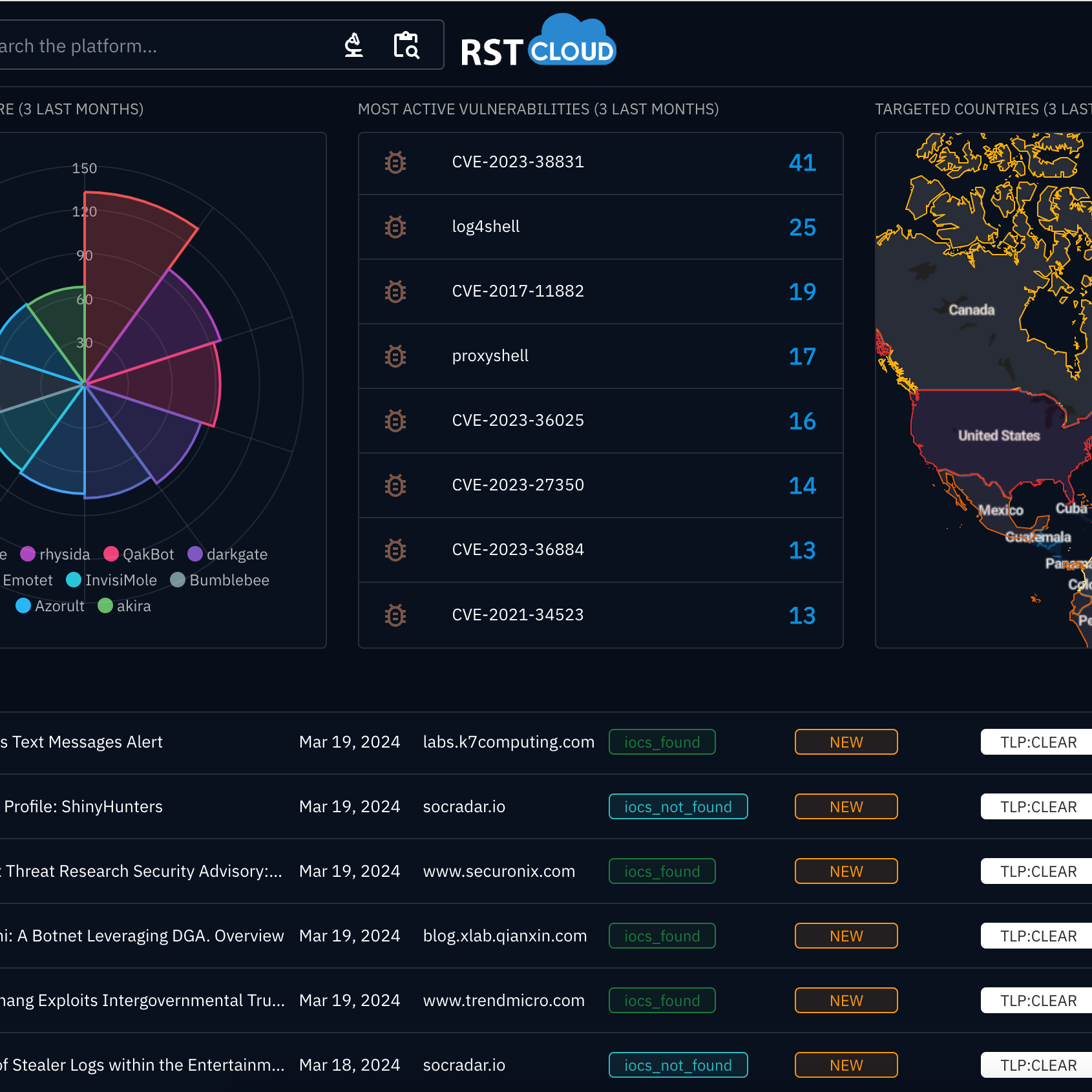

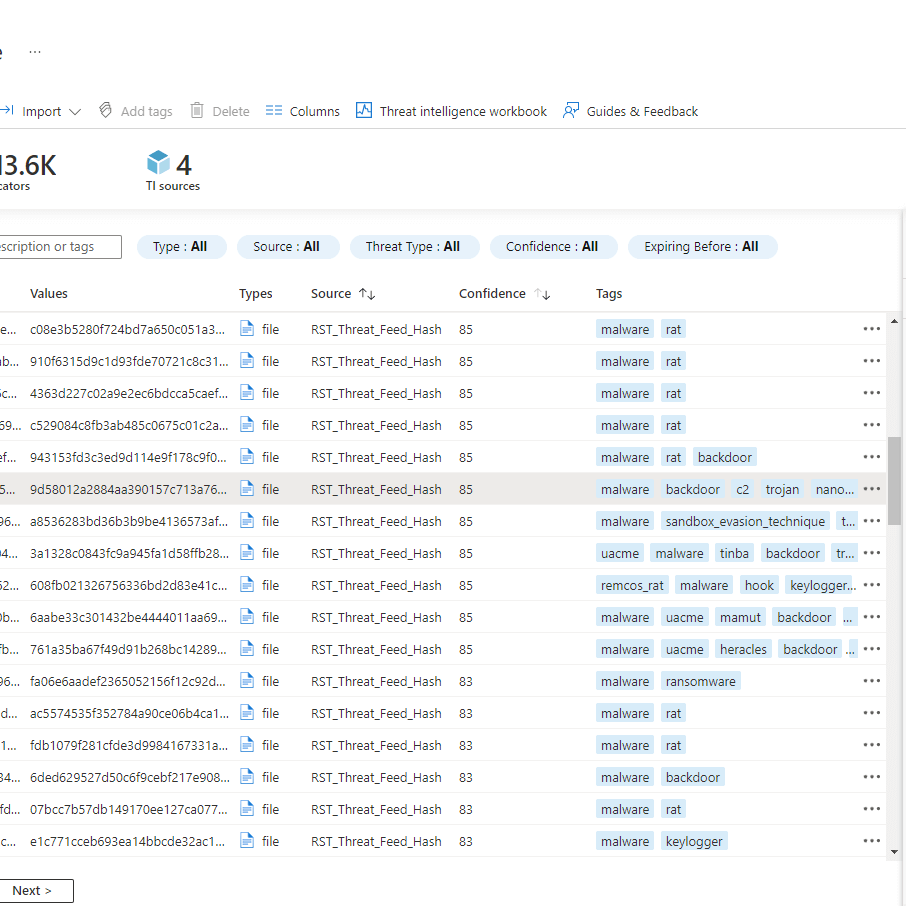
Elevate your security operation with the automated RST Threat Feed integration in Microsoft Sentinel
Integrate the RST Threat Feed into Microsoft Sentinel for automated threat intelligence. Leverage STIX v2.1/TAXII, and Logic Apps for a swift integration, ensuring your security operations are well-equipped to stay ahead of evolving threats. This integration enables quick population of the built-in threat intelligence table in Microsoft Sentinel, providing threat indicators for real-time threat detection.
Key Features:
- Cloud to Cloud integration: Within minutes, threat indicators from the RST Threat Feed flow seamlessly into your workspace
- STIX v2.1 and TAXII Protocol: Obtain the RST Threat Feed in Microsoft Sentinel using STIX v2.1 and the TAXII protocol
- Proactive Threat Detection: Detect risky IOCs, correlate with internal telemetry, and proactively block threats
- Out-of-the-Box Playbooks Integration: Effortless integration with Logic Apps for efficient playbooks using RST IoC Lookup and RST Noise Control
Benefits:
- Enhanced threat detection and response capabilities
- Correlate external and internal threat data seamlessly
- Proactively block potential threats
For full installation and usage instructions, please visit the MS Sentinel Integration Page.
Unlocking Seamless Security with
RST Cloud and Fortinet
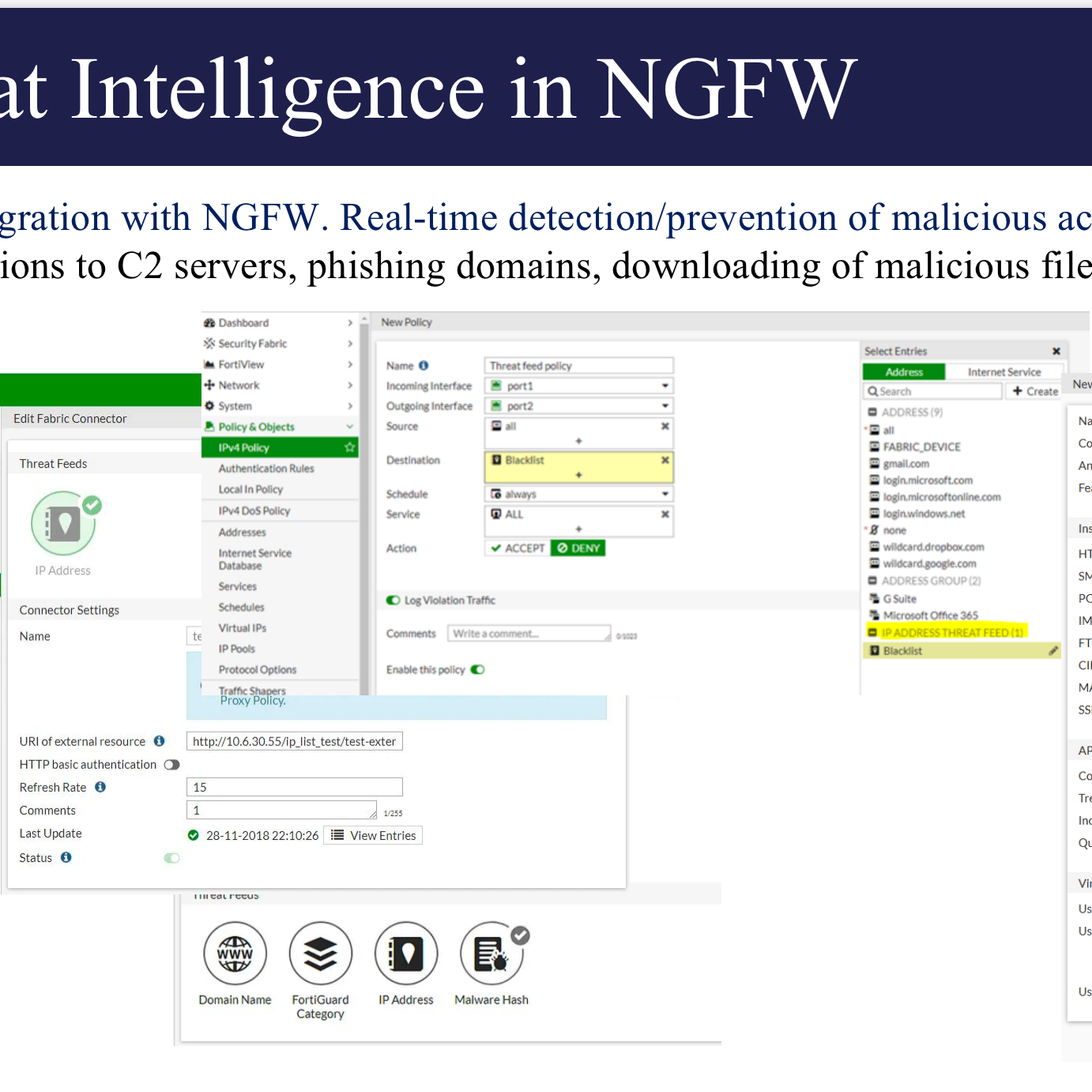
RST Cloud services seamlessly integrate with Fortinet products, including FortiGate and FortiSIEM. Among these integrations, the RST Threat Feed emerges as a valuable source of Cyber Threat Intelligence (CTI) data, specifically tailored for Fortinet products.
Key Integration Features:
- FortiSIEM Integration:
- Leverage RST Threat Feed in FortiSIEM for real-time threat detection, investigation, and proactive threat hunting.
- FortiGate Integration:
- Directly integrate RST Threat Feed into FortiGate for real-time blocking of malicious traffic at the network level.
- Real-time Deep Web Intelligence:
- Receive real-time threat intelligence from the vast number of sources across the globe, enabling the benefit of protection rules and swift, confident actions.

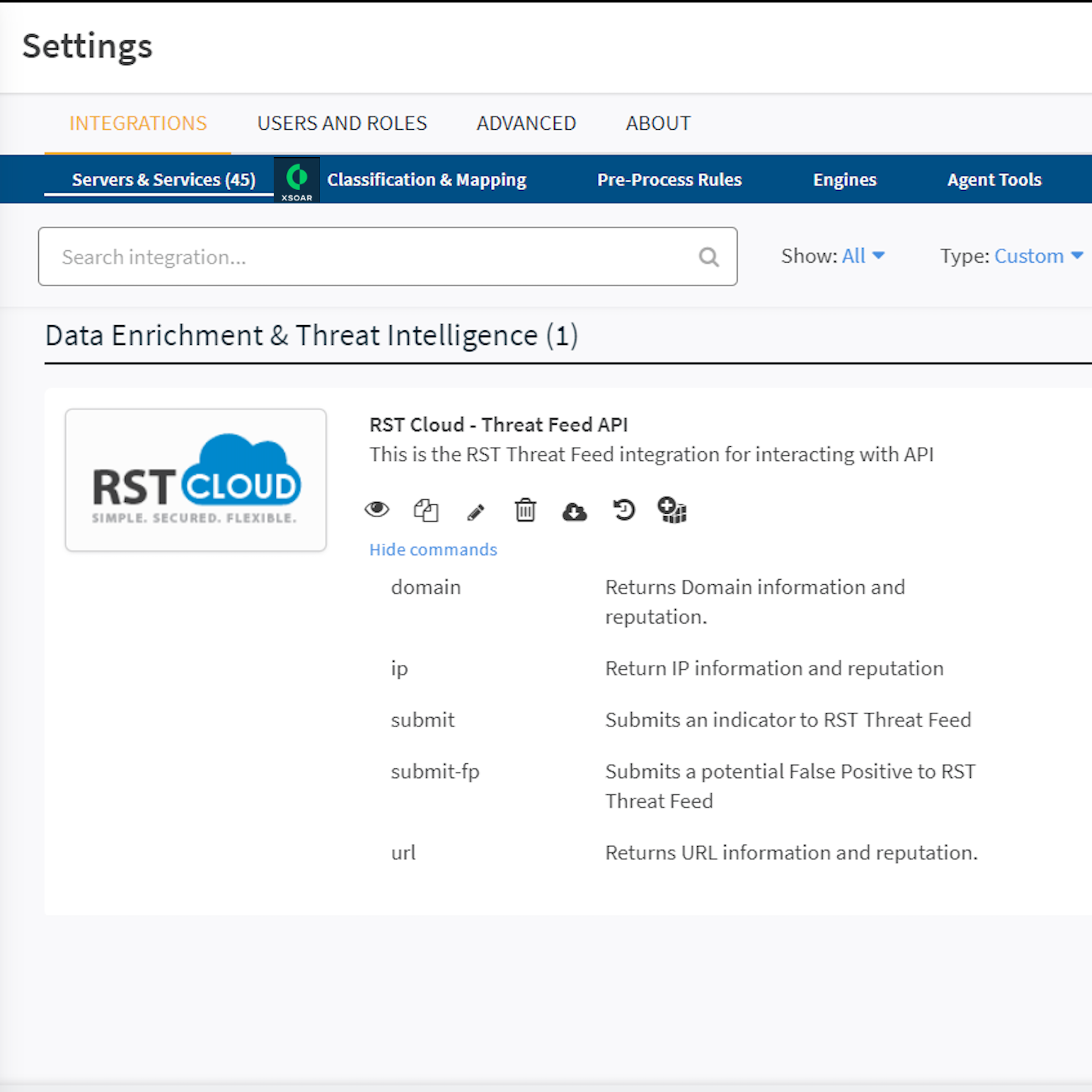
Unleash advanced Threat Intelligence capabilities in
RST Threat Feed collaboration with Cortex XSOAR
As an esteemed Cortex XSOAR partner, RST Cloud offers an unparalleled suite of capabilities through its high-fidelity threat intelligence database, seamlessly accessible via API. This comprehensive solution empowers security professionals to conduct real-time scrutiny for domains, URLs, IP addresses, and hashes, encompassing a wide spectrum of threat categories such as Phishing, Web Attacks, C2 Servers, Botnets, Malware, TOR nodes, Scanning Hosts, Bad Bots, DDoS, Cryptomining, Spamming Hosts, Fraud, and more.
Key Features:
- API Integration Pack:
- The comprehensive API integration pack is designed for flexibility and efficiency, offering:
- Real-time checking for IP, Domain, URL, or Hash.
- Functions to submit new indicators to the cloud.
- Capability to submit potential false positive Indicators of Compromise (IoC).
- The comprehensive API integration pack is designed for flexibility and efficiency, offering:
- Enrichment Playbooks:
- RST IoC Lookup streamlines threat intelligence utilisation with specialised playbooks catering to IP, Domain, URL, and Hash enrichment. These playbooks ensure a structured and efficient approach, enhancing the efficacy of security operations.
- Individual Scoring Mechanism:
- RST IoC Lookup employs an intricate individual scoring mechanism. Each indicator is assigned a score based on qualitative and quantitative parameters, including indicator type, reporting entity, community awareness, historical exposure, and other relevant factors.
For full installation and usage instructions, please visit the Cortex XSOAR marketplace.
Unlocking Seamless Security with
RST Cloud and Splunk
Improve visibility across hybrid environments by leveraging the capabilities of threat intelligence offered by RST Cloud and Splunk platform. The RST Threat Feed App for Splunk enables the extraction of data from the RST Cloud API, saving it in Splunk for subsequent events lookup usage.
After installation, the app provides IoCs of types: IP, domain, URL, hash. It oversees download, update, and cleanup tasks to ensure the lookups are up-to-date on a daily basis.
The app includes four general detection rules (alerts) to demonstrate the effective utilisation of Threat Intelligence data in your searches.
By effortlessly integrating internal logs with external threat intelligence, users acquire crucial insights and a holistic perspective on potential threats.
Benefits:
- Utilise risk lists to inform correlation rules
- Access correlation dashboards tailored to specific use cases
- Leverage pre-built use cases and security dashboards
- MITRE ATT&CK TTPs, threat/APT attribution of IoCs, full enrichment and environment data
For comprehensive installation and usage instructions, please visit the Splunk Integration Page.
RST Threat Feed App for Splunk is available on the Splunk App Store and can be easily installed and configured by Splunk users.


Welcome to a New Era in cybersecurity with
SAF and RST Cloud integration
Empower the SAF platform with invaluable high-quality Cyber Threat Intelligence (CTI) knowledge from RST Cloud. Our seamless integration of RST Threat Feed and RST Report Hub products into the SAF monitoring platform introduces a revolutionary approach to handling security incidents. Unlock a myriad of possibilities, including real-time incident detection, detailed indicator insights, and comprehensive Tactics, Techniques, and Procedures (TTPs) used by threat actors. Access other valuable contextual information such as data from APT reports directly within the monitoring platform.
Key Benefits:
- Quicker Decision-Making: Experience enhanced incident triage with real-time actionable insights, resulting in quicker decision-making during security incidents.
- Workflow Optimisation for SOC Analysts: Significantly optimise the workflow of SOC analysts by saving valuable time. Streamline the decision-making process, allowing analysts to access required Threat Intelligence (TI) data seamlessly within the SAF UI, eliminating the need to switch between different screens.
- Efficient CTI Service Integration: Enable the SAF platform with CTI services efficiently and user-friendly. This integration ultimately enhances the security posture of organisations, raising cybersecurity standards.
- Exploration of Advanced Scenarios: Explore incident response capabilities, Threat Hunting, and other scenarios designed to maximise the utilisation of RST Cloud’s data within the SAF platform.
For full installation and usage instructions, please visit the SAF-Systems Integration Page
Get Free Trial
Choose a product and get your trial account by email. By signing up for a free trial, you grant RST Cloud permission to contact you via the provided email address for purposes related to your trial, account management, and relevant product information.