What Threats to Watch Out For in February 2023
Our recent data analysis of the Threat Feed database from January highlights key updates on active threats that should be monitored closely. Whether you are an individual, a business, or a government entity, the information presented here is essential reading.
We see a noticeable increase in the number of indicators attributed to these specific threats frameworks:
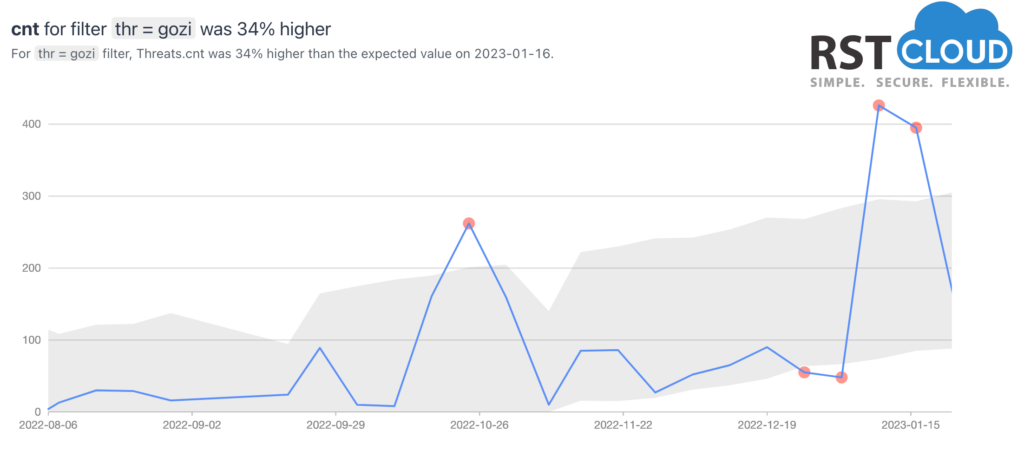
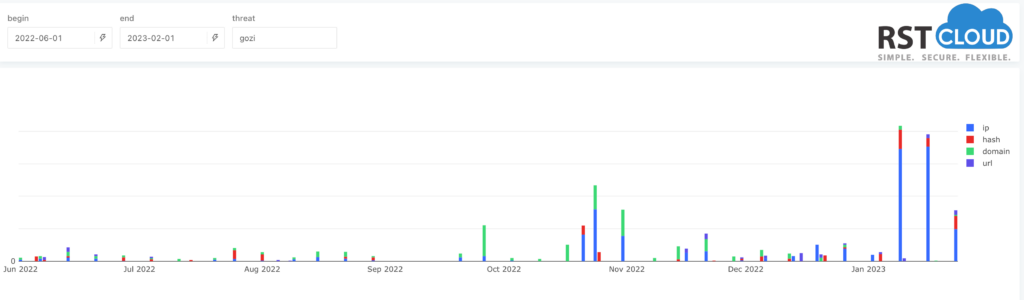
- Gozi Trojan,
- Sliver Framework,
- Raccoon Stealer,
- Quasar RAT,
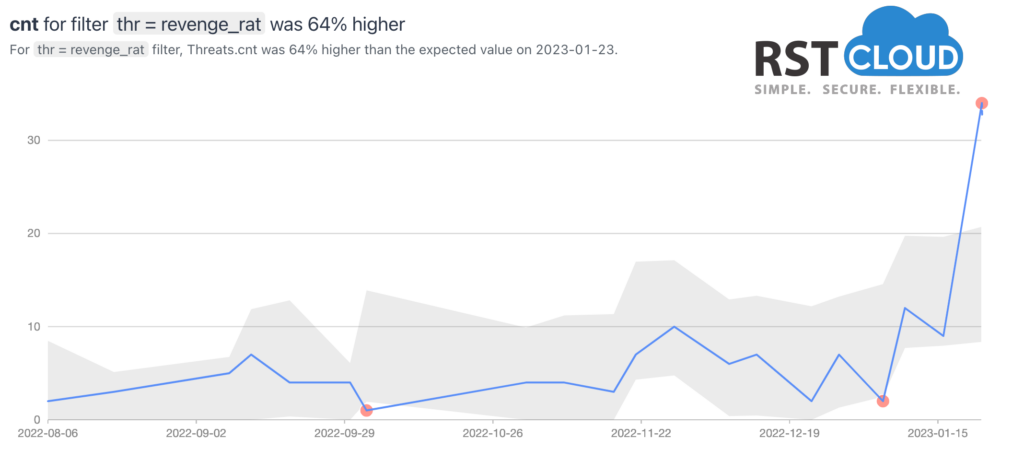
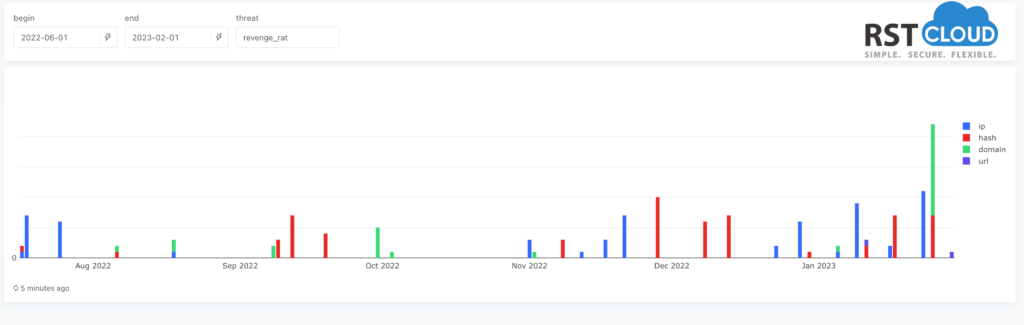
- Revenge RAT.
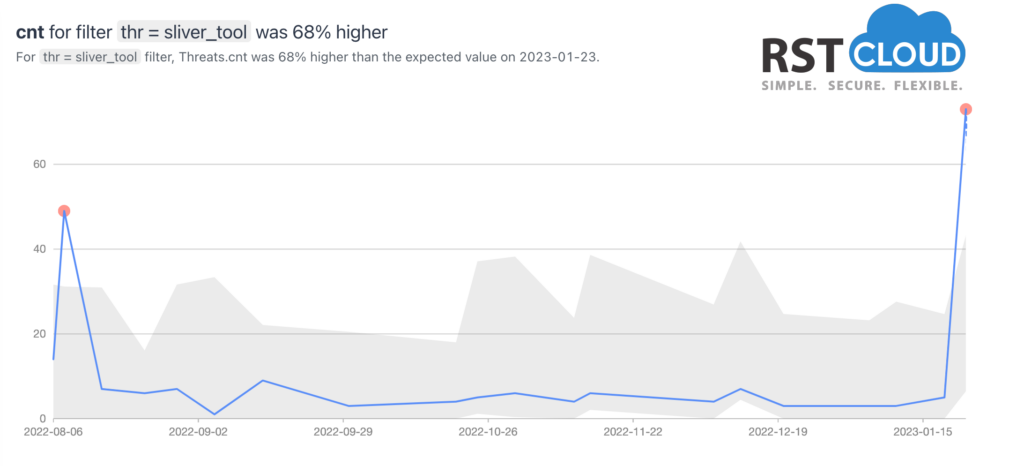
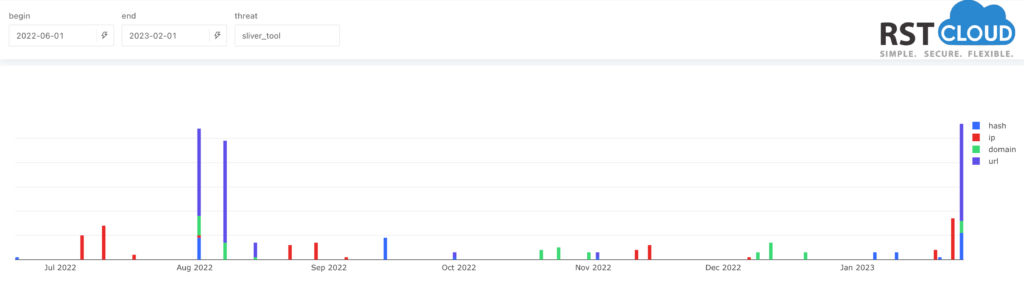
The Sliver framework has gained increased attention from threat actors and its associated malware has been increasingly delivered with its Command & Control (C2) capabilities.
Gozi is a banking Trojan also known as RM3, ISFB, Ursnif, Dreambot, CRM, and Snifula, and can be considered as a group of malware families that are based on the same malicious codebase. Despite being frequently updated, January’s analysis suggests that it has received multiple updates to its network infrastructure. These insights provide valuable context for those monitoring the threat.
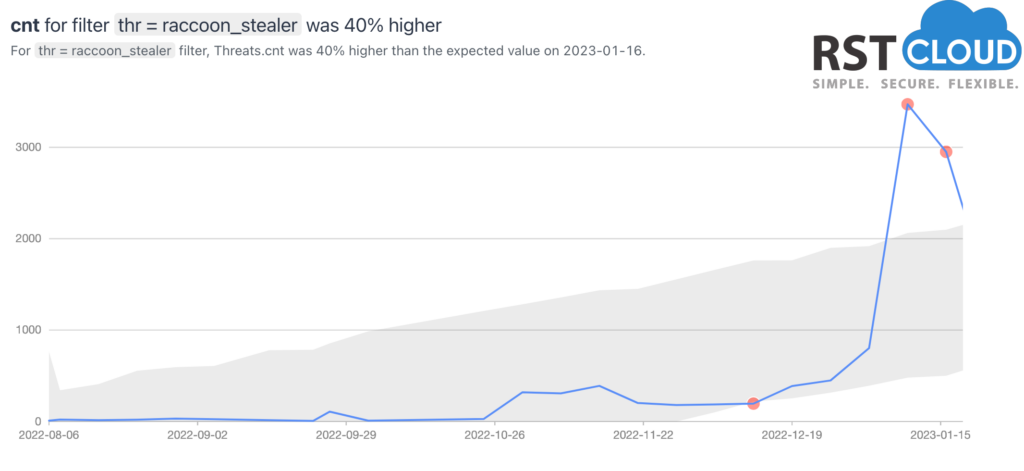
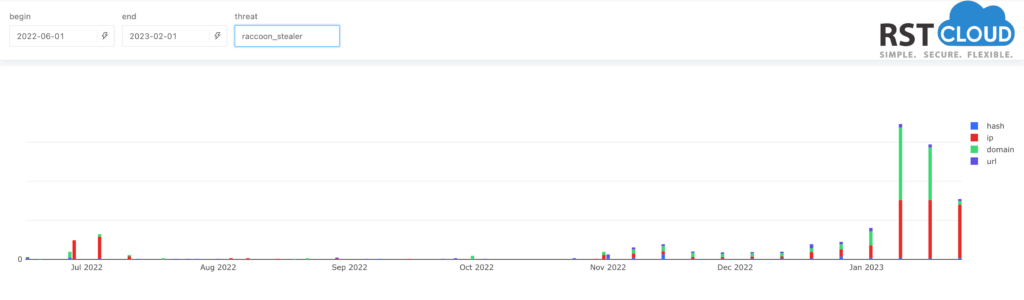
Raccoon Stealer is a malware-as-a-service tool. It gathers personal information including passwords, browser cookies and autofill data, cryptowallet details and other sensitive information from victims, and also records system information such as IP addresses and geo-location data etc.
Raccoon’s two most popular delivery methods are phishing campaigns and exploit kits. Once data is located on the target system, it is eventually placed into a .zip file and sent to the malware Command and Control (C&C) server. Its operators are constantly innovating and after claiming the new version (Raccoon Stealer 2.0) at May of 2022 this is the first recognisable update that we saw for this malware.
Sliver is the Go-based security testing tool developed by researchers at BishopFox cybersecurity company. Some security agents notes that hackers, from state-sponsored groups to cybercrime gangs, are more and more using this tool in attacks as replacement for Cobalt Strike software. Sliver is a Command and Control (C2) system made for penetration testers, red teams, and advanced persistent threats and we saw huge rise of network indicators connected to this software.
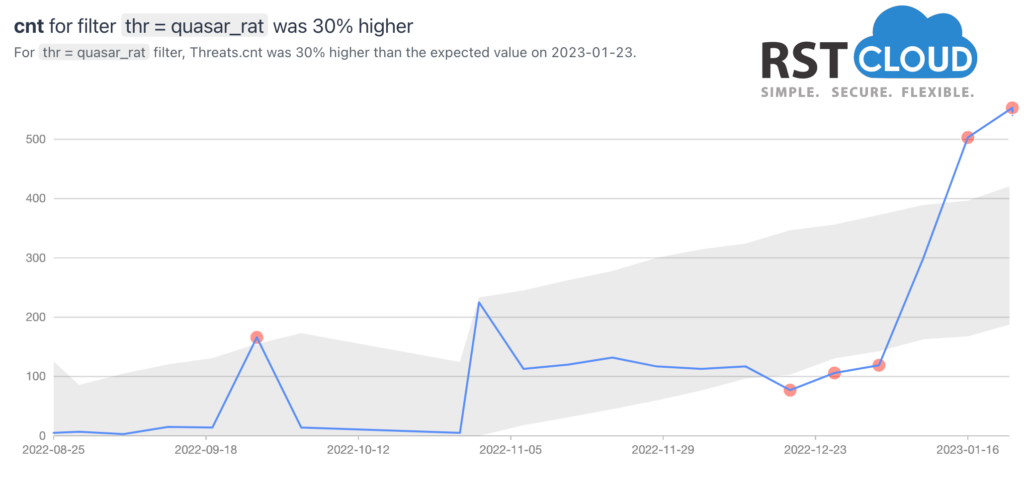
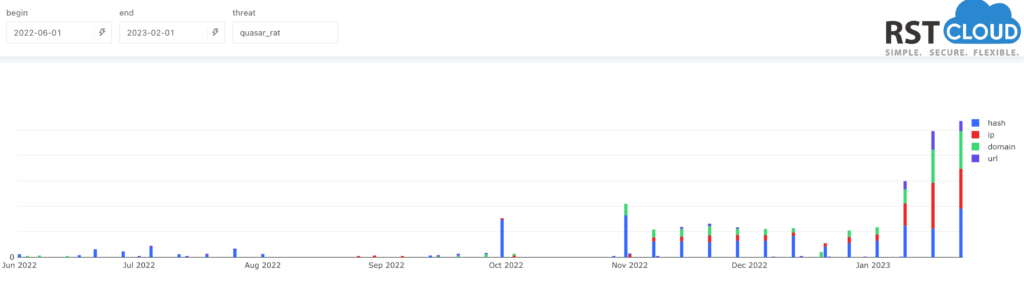
Quasar is a legitimate open-source remote administration tool (RAT). Still it’s been observed being used maliciously by Advanced Persistent Threat (APT) actors for cybercrime and cyber espionage campaigns.
Quasar does not contain software vulnerability exploits by itself. But it can be used to steal personal information, remotely control other computers over a network or other malicious purposes.
Revenge RAT is a simple and freely available Remote Access Trojan, first observed in 2016, that automatically gathers system information and allowing threat actors to remotely access system components such as webcams, microphones, and various other utilities. Through Revenge RAT malware, threat actors can remotely execute malicious tasks on the user’s computer and steal any sensitive data available to them, or even spy users by capturing keystrokes, watching them via webcam, or even listening to their microphones
As we can see from our statistics, their infrastructure has been updated and renewed last month.