Integrating Palo Alto Networks Firewall
Organisations can seamlessly integrate RST Cloud's powerful threat intelligence with Palo Alto Networks' cutting-edge solutions.
Many network security vendors allow to enhance their threat detection and prevention capabilities by integrating multiple external threat intelligence sources, such as RST Cloud.
RST Cloud seamlessly integrates with Palo Alto Networks NGFWs through the External Dynamic List (EDL) feature, enabling organisations to harness the collective intelligence of the global cybersecurity community within their network protection infrastructure. By prioritising critical EDLs, organisations can optimise system resources and proactively block threats at the network perimeter.
Prerequisites:
- API keys obtained from the RST Cloud team (contact us on info@rstcloud.net or via the website contact form)
- For Palo Alto guidance on EDL, please refer to the documentation (PAN-OS 11.1) page.
Leveraging the RST Cloud API for Palo Alto NGFW
To facilitate seamless communication between RST Cloud and Palo Alto NGFW, a special API interface is utilised. The RST Threat Feed API for Palo Alto supports HTTP GET requests with Transport Layer Security (TLS) and basic authentication access. The data is returned in the format that NGFW natively understands.
Organisations can leverage this API to retrieve threat intelligence data from RST Cloud and integrate it strait into their NGFWs, ensuring comprehensive protection against emerging threats.
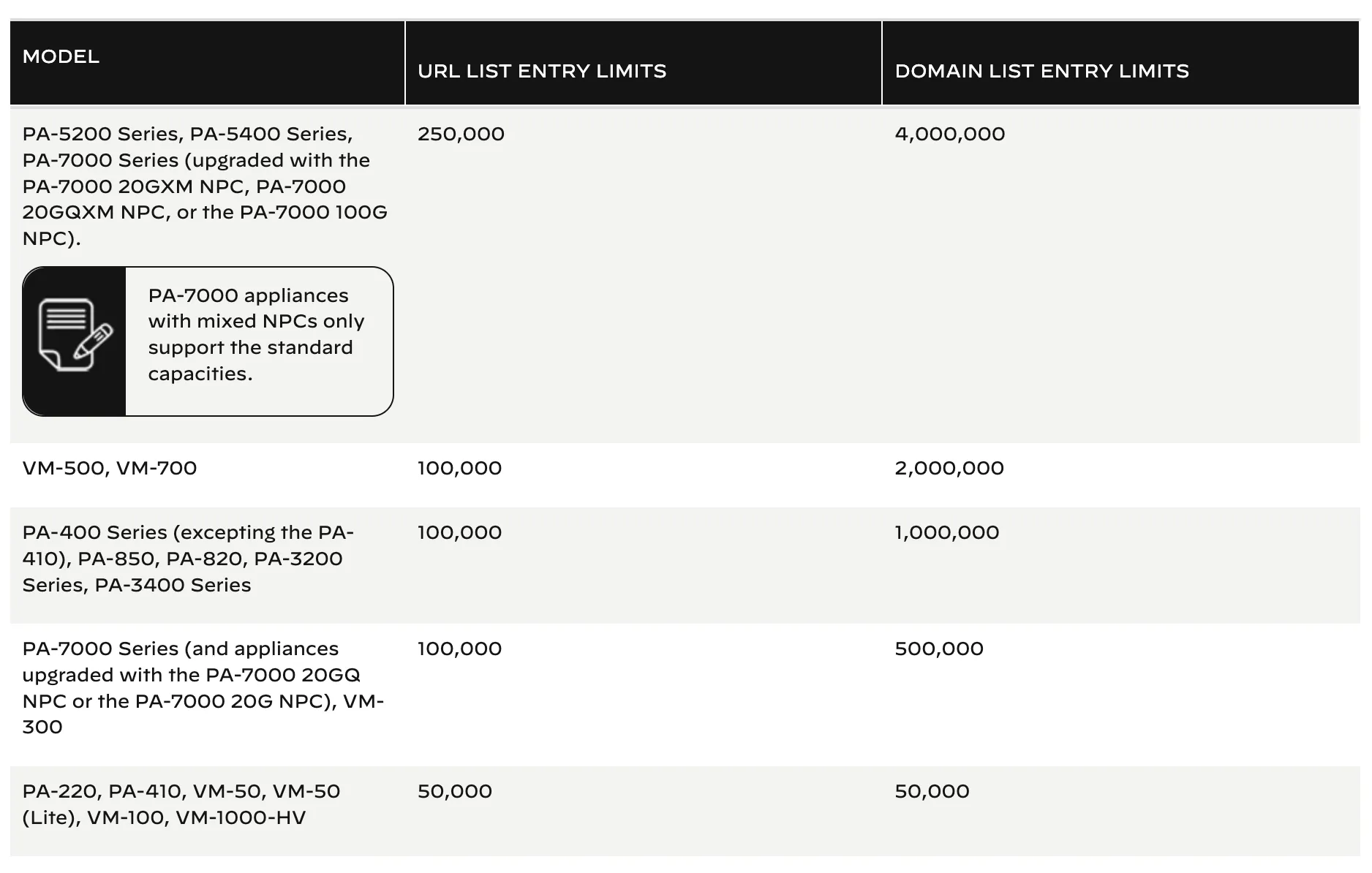
The API supports integration with all device versions that support EDL feature:
Palo Alto firewalls dynamically import the list at regular intervals, enabling up-to-date policy enforcement without requiring configuration changes. In case of connectivity issues, the firewall continues to enforce the last successfully retrieved list until the connection is restored.
Configuration steps:
Create EDL for RST Threat Feed fetching:
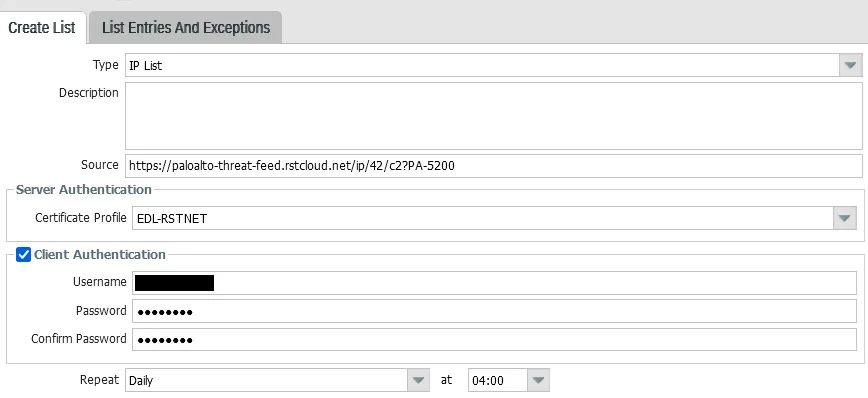
The structure of the request:
https://api.rstcloud.net/v1/integrations/paloalto/[feed_type]/[category][minimum score]?model=[your PA model].
indicator_type (mandatory): ip, domain, url
score (mandatory): from 0 to 100
category (optional, requires score to be specified): all, backdoor, badbot, banker, bootkit, botnet, c2, clicker, cryptomining, ddos, dns, downloader, drainer, dropper, fraud, generic, keylogger, malware, phishing, proxy, raas, ransomware, rat, rootkit, scam, scan, screenshotter, shellprobe, spam, spyware, stealer, tor_exit, trojan, vpn, vulndriver, webattack, wiper
model (optional):
PA-220,PA-410,VM-50,VM-50-Lite,VM-100,VM-1000-HV,PA-7000,VM-300,PA-400,PA-850,PA-820,PA-3200,PA-3400,VM-500,VM-700,PA-5200,PA-5400,PA-7000
Examples:
Fetch malicious IP addresses with score more than 50:
https://api.rstcloud.net/v1/integrations/paloalto/ip/50?model=default
Fetch malicious C2 IP addresses with score more than 40:
https://api.rstcloud.net/v1/integrations/paloalto/ip/40/c2?model=default
Fetch malicious domains with score more than 50:
https://api.rstcloud.net/v1/integrations/paloalto/domain/50?model=default
Fetch URLs with score more than 50:
https://api.rstcloud.net/v1/integrations/paloalto/url/50?model=default
To use the IP addresses for the use case of protection your internal resource from external attacks:
https://api.rstcloud.net/v1/integrations/paloalto/ip_src/50?model=default
To further enhance threat intelligence integration, RST Cloud recommends selecting a minimal score for indicators to control what data is to be imported. Without specifying a category, for IP addresses, Domains, and URLs a recommended score threshold is 50.
The score assist in prioritising higher-risk indicators, enabling organisations to focus on blocking the most critical threats.
Users seeking access to all available Indicators of Compromise (IoCs) can use a score of 0 (not recommended). Another scenario is to use a specific list for C2, another for Tor addresses and so on, so, you can set individual score on per category basis as well.
Congratulations! You have successfully configured the RST Threat Feed in Palo Alto Networks solutions. You can now leverage the threat intelligence data in your security operations.
The integration of RST Threat Feed with Palo Alto NGFW empowers real-time threat detection and prevention within NGFW modules, providing an effective defence against network threats. Leveraging high-confidence indicators from RST Cloud, this integration enhances mitigation of malicious activities. By utilising threat intelligence across multiple Palo Alto NGFW modules, organisations can block threats based on IP, domain, and URL indicators, ensuring comprehensive protection against malicious network connections.