Improving the threat intelligence process in Splunk with RST Cloud
Jan 8, 2023
Splunk is designed to handle large volumes of data, but this can also make it difficult to identify real threats among all the noise. Integrating threat intelligence feeds into Splunk can be difficult, and may require custom scripting or the use of third-party add-ons.
RST Cloud offers an app for Splunk that allows users to seamlessly integrate threat intelligence feeds into the Splunk platform. This enables users to have real-time access to detect, investigate and hunt for potential threats, without the need for expensive Splunk Enterprise Security licenses. The app aims to mitigate common issues such as difficulties integrating feeds, lack of context, and manual processes associated with threat intelligence by providing a user-friendly and efficient solution.
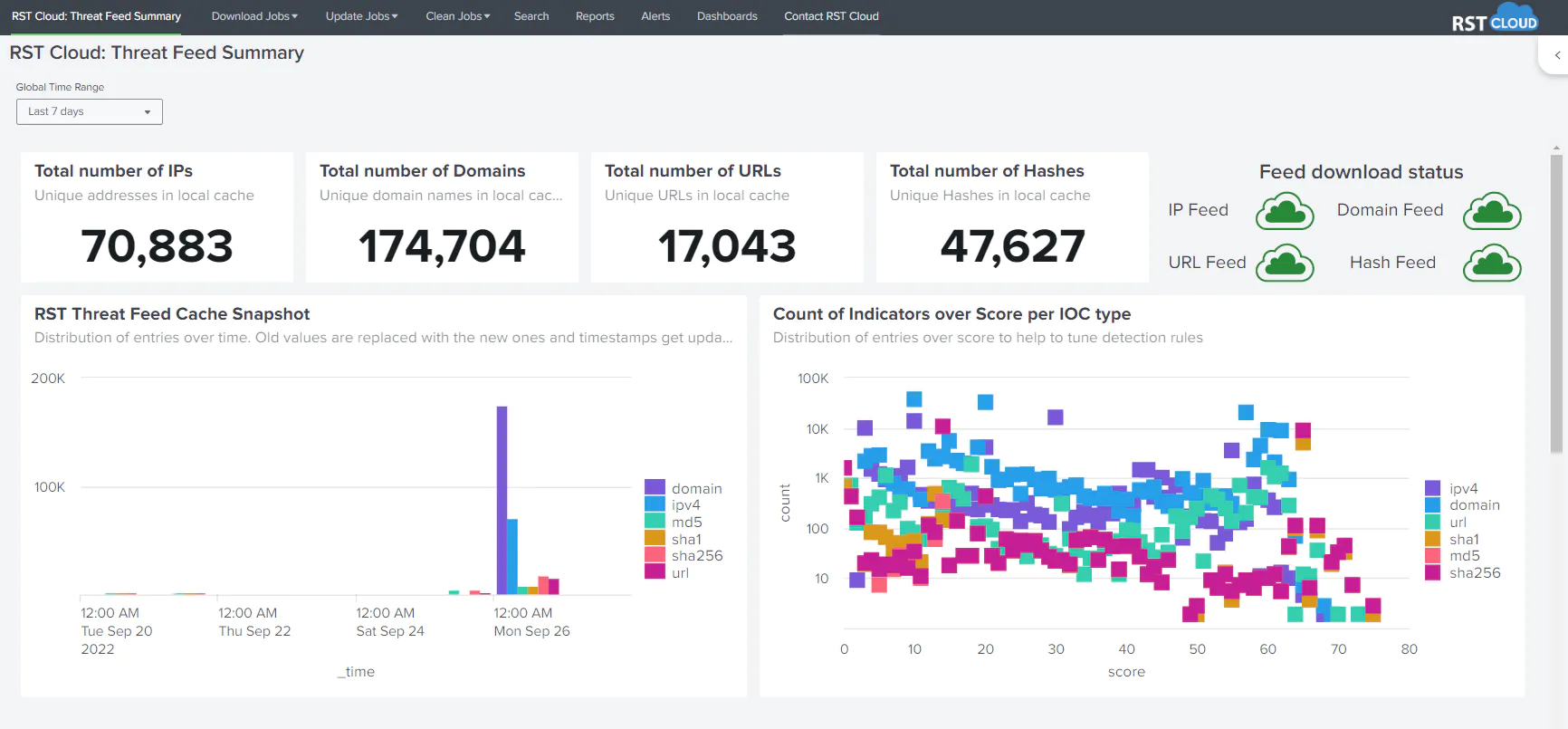
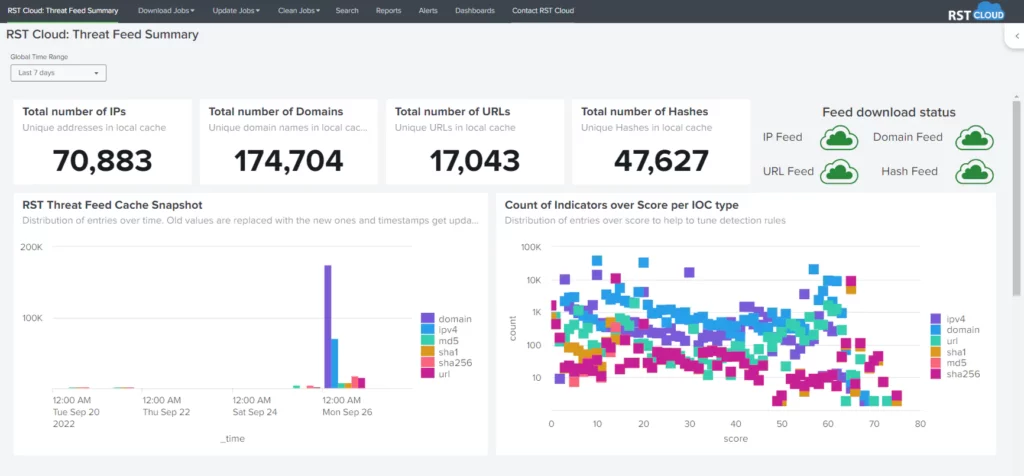
RST Cloud’s Threat Feed includes a wide range of indicators across multiple categories, such as Phishing, Web Attacks, Command and Control servers, Botnets, Malware, TOR nodes, Scanning Hosts, Bad Bots, DDoS, Cryptomining, Spamming Hosts, Fraud, and more. This intelligence is sourced from various sources like private and open-source feeds, in-house systems, public online sandboxes, and RST Cloud’s own honeypot network. These feeds allow Splunk users to use the platform’s analytics and visualization capabilities for real-time detection and investigation of potential threats, as well as proactive hunting. The feed includes various types of indicators such as IP, Domain, URL, md5, sha1, and sha256.
RST Threat Feed App for Splunk (https://splunkbase.splunk.com/app/6616) is available on the Splunk App Store and can be easily installed and configured by Splunk users. For installation make the following steps:
- Configure downloading of the files and its decompression into a directory $SPLUNK_HOME/etc/apps/[app_name]/lookups/
[rst_threat_feed_ip]
filename = ioc_ip_latest.csv
[rst_threat_feed_domain]
filename = ioc_ip_latest.csv
[rst_threat_feed_url]
filename = ioc_url_latest.csv
[rst_threat_feed_hash]
filename = ioc_hash_latest.csv- Create a script and add it to CRON to be downloaded daily (update paths and variables/placeholders):
#!/bin/bash
cd $SPLUNK_HOME/etc/apps/[app_name]/lookups/
curl -L -X GET -H "Accept:*/*" -H "x-api-key:API_KEY" 'https://api.rstcloud.net/v1/ip?type=csv&date=latest' -o ioc_ip_latest.csv.gz
curl -L -X GET -H "Accept:*/*" -H "x-api-key:API_KEY" 'https://api.rstcloud.net/v1/domain?type=csv&date=latest' -o ioc_domain_latest.csv.gz
curl -L -X GET -H "Accept:*/*" -H "x-api-key:API_KEY" 'https://api.rstcloud.net/v1/url?type=csv&date=latest' -o ioc_url_latest.csv.gz
curl -L -X GET -H "Accept:*/*" -H "x-api-key:API_KEY" 'https://api.rstcloud.net/v1/hash?type=csv&date=latest' -o ioc_hash_latest.csv.gz
gzip -d *.gz- Restart or reload Splunk configuration with debug/refresh
After the app is installed, you may want to manually run once download/update jobs to initialise the lookups or wait for the scheduled jobs to populate it for you around 02:00 AM UTC
The App contains download/update/cleanup jobs to maintain the lookups on the daily basis.
The App for RST Threat Feed is used to download data from RST Cloud API and saves it into Splunk lookups for further usage.
For example, if you save those files into the default app named “search”, you shall see:
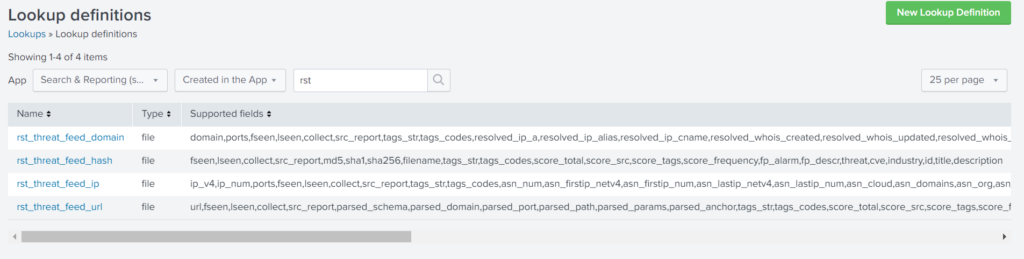
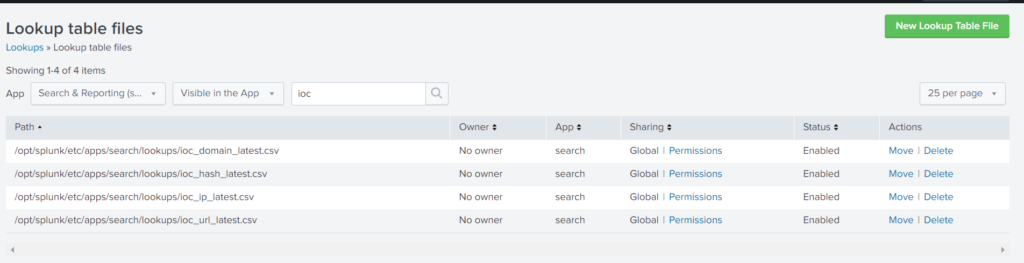
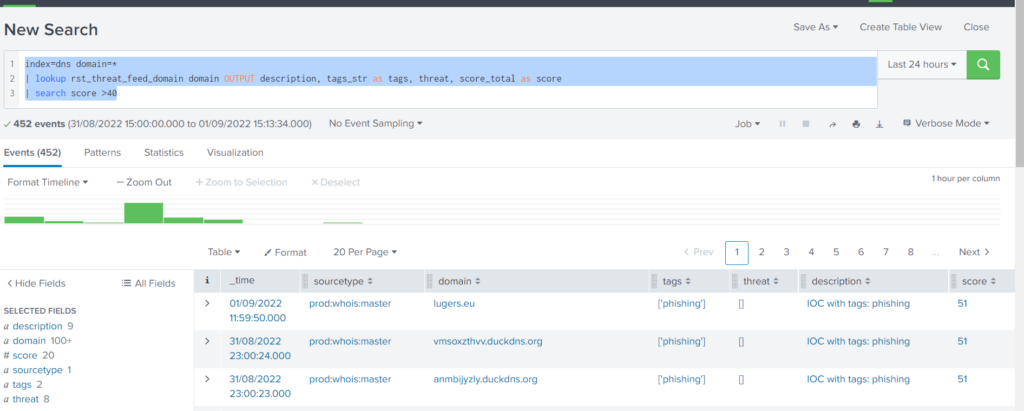
To use the data, just search and use the “lookup” command. For example, to enrich domains use:
… | lookup rst_threat_feed_domain domain OUTPUT description, tags_str as tags, threat, score_total as score
To search for malicious domains use any of the supported fields. For example, score > 40
index=dns domain=*
| lookup rst_threat_feed_domain domain OUTPUT description, tags_str as tags, threat, score_total as score
| search score >40
Each indicator has an individual score calculated based on its actuality and risk: what type of the indicators it is, who is the reporter of the indicators, how many others are already aware of that indicator, was that indicator exposed previously and many other contributing factors.
We recommend to use total score more than 50-55 if you want to receive only actual dangerous IoCs. For suspicious indicators use score between 35-40 and 50-55, and for informative one less than 40.
RST Threat Feed App contains 4 detection rules (alerts) to demonstrate how to use Threat Intelligence data in your searches. RST Threat Feed App is also shipped with health reports and dashboards and includes sample detection rules.
For more information, visit our Splunk Integration page.
A trial key can be obtained from https://www.rstcloud.com/trial or just contact as through trial@rstcloud.net email.