FortiGate Integration
FortiGate firewalls become far more effective when paired with high-quality threat intelligence. By integrating RST Cloud’s trusted threat feeds, FortiGate can automatically block more malicious IPs, domains, URLs, and file hashes in real time.
This integration uses the External Block List feature to pull indicators directly from RST Cloud. These indicators can then be applied to firewall policies, DNS filtering, or web filtering, enabling proactive threat prevention without manual input.
The steps below explain how to connect RST Cloud to your FortiGate and start using this data immediately.
For more information on integrating other Fortinet products, refer to this page.
Feel free to reach out to us and request a free evaluation of this integration at trial@rstcloud.net
About this integration
RST Cloud offers a number of APIs that can be used to interface with a range of enterprise products. The FortiGate integration model leverages a specially built API designed for firewalls, ensuring device compatibility. In a nutshell, the API interaction is a TLS-encrypted HTTP GET request with login/password access:
For Internal -> External Blocklists:
GET https://[username]:[password]@api.rstcloud.net/v1/integrations/fortigate/[indicator_type]/[score]/[category],
indicator_type (mandatory): ip, ip_src, domain, url, md5, sha1, or sha256
score (mandatory): from 0 to 100
category (optional, requires score to be specified): all, backdoor, badbot, banker, bootkit, botnet, c2, clicker, cryptomining, ddos, dns, downloader, drainer, dropper, fraud, generic, keylogger, malware, phishing, proxy, raas, ransomware, rat, rootkit, scam, scan, screenshotter, shellprobe, spam, spyware, stealer, tor_exit, trojan, vpn, vulndriver, webattack, wiper
Example of Internal -> External Blocklists requests:
https://api.rstcloud.net/v1/integrations/fortigate/ip/50/c2
https://api.rstcloud.net/v1/integrations/fortigate/domain/50
https://api.rstcloud.net/v1/integrations/fortigate/url/50
https://api.rstcloud.net/v1/integrations/fortigate/md5/60/malware
Example of External -> Internal Blocklists requests:
https://api.rstcloud.net/v1/integrations/fortigate/ip_src/40
https://api.rstcloud.net/v1/integrations/fortigate/ip_src/30/webattack
An administrator can take advantage of the feed’s capabilities in two ways.
First and foremost, use the scoring modelling results to block only “high” score indicators. If you don’t pick a category, we recommend treating IoCs with a score less than 45 as informational, between 45 and 55 as suspicious, and IP addresses with a score bigger than 55 as malicious. Those score thresholds differ depending on the type of IoC. A good starting point for blocking utilising external domain lists is a score of 50. The query’s versatility allows administrators to choose which types of indicators they require and to find a score that best meets their needs. RST Cloud customers tend to set a score threshold higher for IP addresses, but it might be a lower value of the score used to classify an IoC as risky for Domain/URL types and especially hashes.
Second, indicator categories can be used to create custom lists to block ransomware or phishing-related connections, with the option of lowering the score for those categories and expanding the coverage.
FortiGate Configuration Steps
IoC types: IP, Hostname, URL
External Block List is the feature that FortiGate uses to integrate with external sources of threat intelligence. This used to pull a list of indicators from a remote server and import them into a device. You can use External Block List (Threat Feed) for web filtering and DNS, or in firewall policies. Policy support for external IP list used as source/destination address.
A FortiOS can be configured to import indicators from RST Cloud based on two following criteria: score (from 0 to 100) and category (malware, c2, phishing, etc.)
Sample configuration for IP list will be:
In Security Fabric > Fabric Connectors > Threat Feeds > IP Address, create or edit an external IP list object.
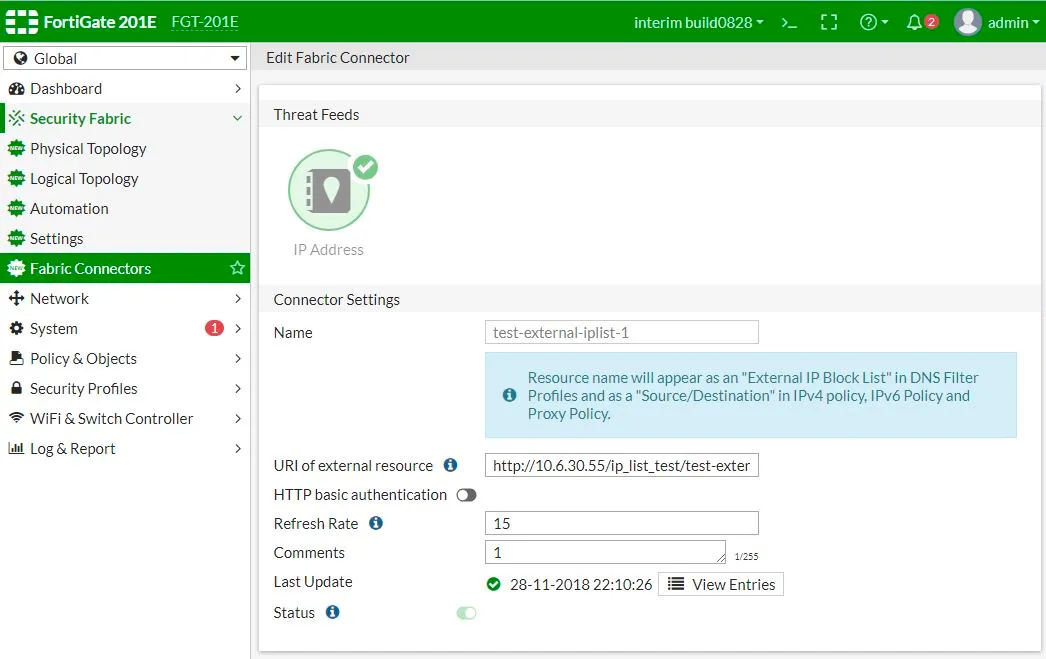
For the URI you should use:
GET https://api.rstcloud.net/v1/integrations/fortigate/[indicator_type]/[score]/[category]
Examples:
https://api.rstcloud.net/v1/integrations/fortigate/ip/55
https://api.rstcloud.net/v1/integrations/fortigate/ip/45/c2
Then you turn on HTTP basic authentication and fill in the User and Password fields.
To create an external iplist object using the CLI:
config system external-resource
edit “RST_Threat_Feed_IP_45_malware”
set status enable
set type address
set username ‘[username]’
set password [password]
set comments ‘fetches indicators with score more than 45 categorized as malware’
set resource “https://api.rstcloud.net/v1/integrations/fortigate/ip/45/malware"
set refresh-rate 1440
next
end
MD5/SHA1/SHA256 Hashes
You can use FortiGate’s Virus Outbreak Prevention engine with RST Threat Feed hash indicators. To configure Malware Hash:
- Navigate to Security Fabric > Fabric Connectors and click Create New.
- In the Threat Feeds section, click Malware Hash.
The Malware Hash source objects are displayed.
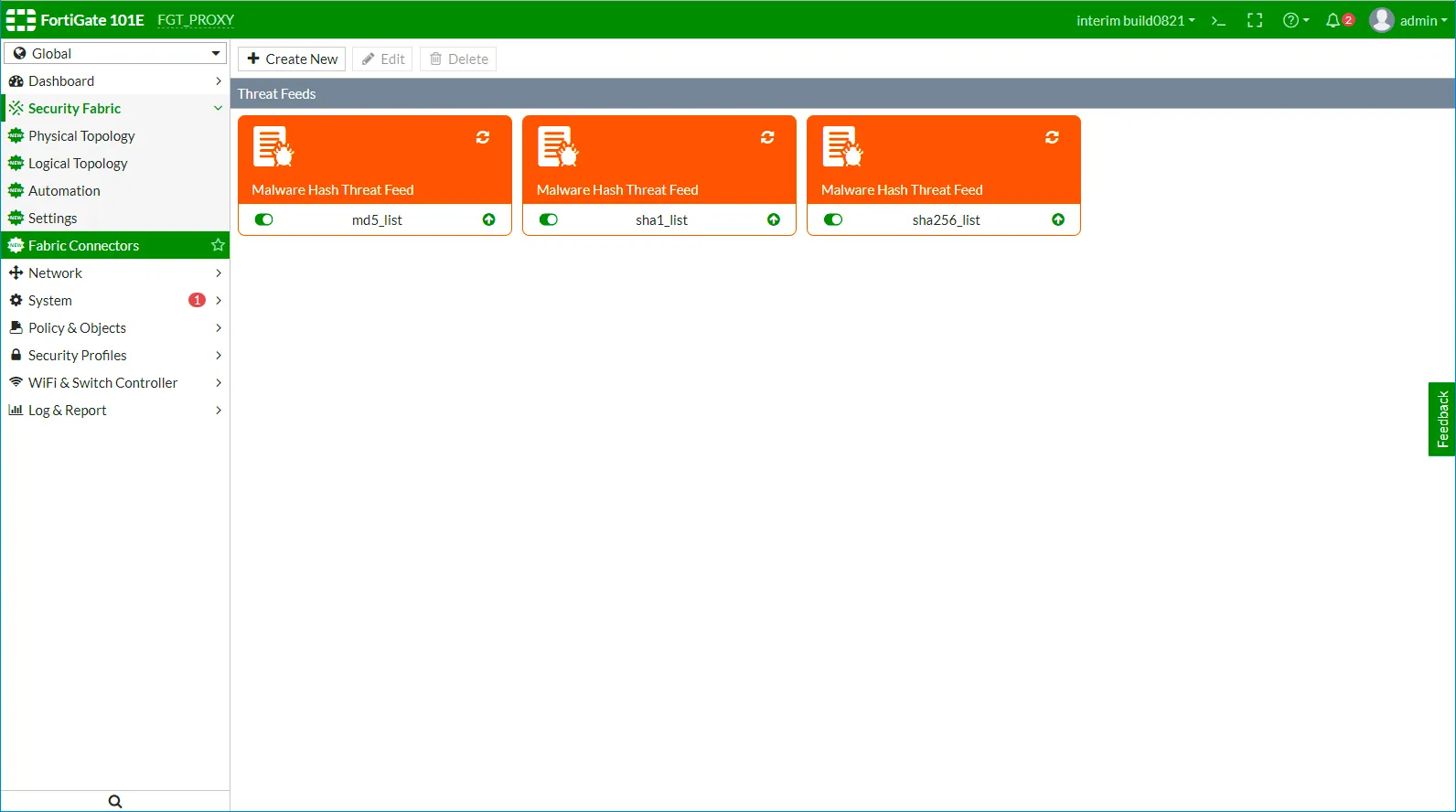
We are a unique feed to support all three hash types (md5, sha1, and sha256) and we enrich each indicator with the missing hash (if it is available) through searching on additional sources, thus normalizing one malware to one indicator with all 3 hashes. As a result, practically most of the indicators have fields for all types of hash functions (all available at the time the indicator is found). But if you want a better security level, you can add all 3 types of hashes to your NGFW policy.
To configure Malware Hash, fill in the Connector Settings section.
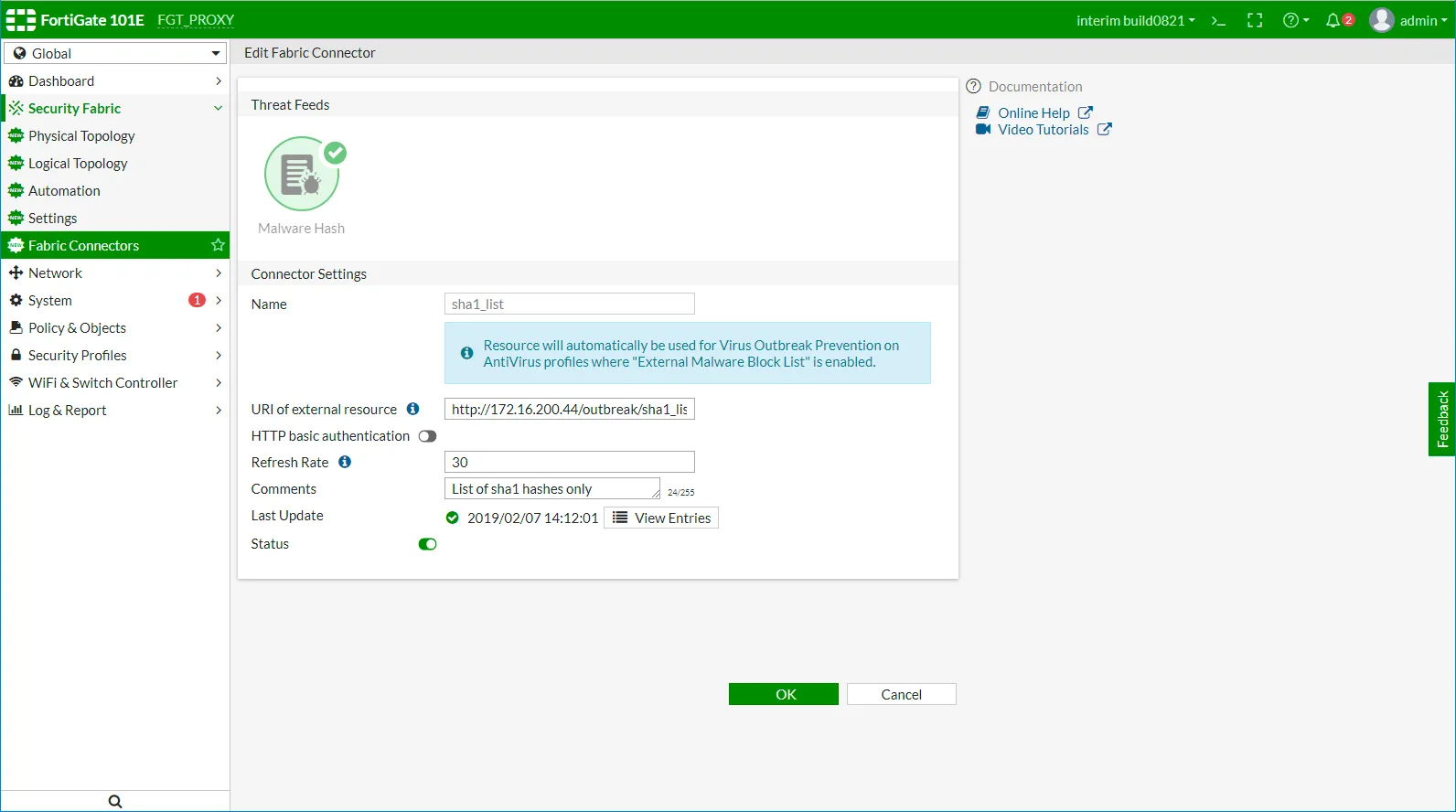
Example URI:
https://api.rstcloud.net/v1/integrations/fortigate/md5/65/malware
Then you turn on HTTP basic authentication and fill in the User and Password fields.
To configure New Malware value for external-resource parameter in CLI:
FGT_PROXY (external-resource) # edit rst_threat_feed_sha1_list
new entry ‘rst_threat_feed_sha1_list’ added
FGT_PROXY (rst_threat_feed_sha1_list) # set type ?
category FortiGuard category.
address Firewall IP address.
domain Domain Name.
malware Malware hash.
To configure external Malware Hash list sources in CLI:
config global
config system external-resource
edit “rst_threat_feed_md5_list”
set type malware
set comments “List of md5 hashes only”
set resource “https://api.rstcloud.net/v1/integrations/fortigate/md5/65/malware"
set refresh-rate 30
next
edit “rst_threat_feed_sha1_list”
set type malware
set comments “List of sha1 hashes only”
set resource “https://api.rstcloud.net/v1/integrations/fortigate/sha1/65/malware"
set refresh-rate 30
next
edit “rst_threat_feed_sha256_list”
set type malware
set comments “List of sha256 hashes only”
set resource “https://api.rstcloud.net/v1/integrations/fortigate/sha256/65/malware"
set refresh-rate 30
next
end
end
Then you can update your AntiVirus Profile with the use of External Malware Block List.