Check Point Integration
To perform real-time threat prevention or detection, RST Threat Feed for NGFW can be utilised by the Check Point NGFW solution to conduct threat intelligence (TI) match searches in the traffic, dropping or alerting on malicious network activities according to policy. The NGFW can use RST Threat Feed to block attacks using high-confidence indicators from RST Cloud and Anti-Virus/ Anti-Bot blades from Check Point. Network threats can be blocked using IP, domain, and URL indicators, and files downloaded from the internet can be checked against file hashes provided by RST Cloud.
About this integration
RST Threat Feed delivers comprehensive coverage across various threat categories, including Ransomware, Phishing, Stealers, Web Attacks, Command and Control servers (C2), Botnets, Malware, VPN, Proxies, and more. Our feed includes key indicators such as IP addresses, domains, URLs, MD5, SHA1, and SHA256 hashes, ensuring broad defence against evolving threats.
We aggregate threat intelligence data from a variety of sources, including private and open-source feeds, social channels, public online sandboxes, and RST Cloud's honeypot network and C2 tracker. This extensive data collection guarantees a robust and dynamic threat intelligence repository.
Check Point users can utilise this relevant TI knowledge to prevent connections to the malicious resources used by threat actors. By integrating the feed into NGFW appliances, users can leverage data that helps stop attackers from gaining access to internal company resources and secure their digital assets.
Check Point Configuration Steps
You can import threat indicator feeds from external sources directly to your Security Gateway. After you import the feeds for the first time and install the policy, the Security Gateway automatically pulls and enforces the indicator file each time the file is updated. The Security Gateway imports the file over HTTPS.
To connect RST Threat Feed into Check Point NGFW you need to:
-
- In the SmartConsole main view, go to Security Policies > Threat Prevention > Custom Policy/Autonomous Policy. In the bottom left section, go to Custom Policy Tools/Autonomous Policy Tools > Indicators. Click New and select External IoC feed:
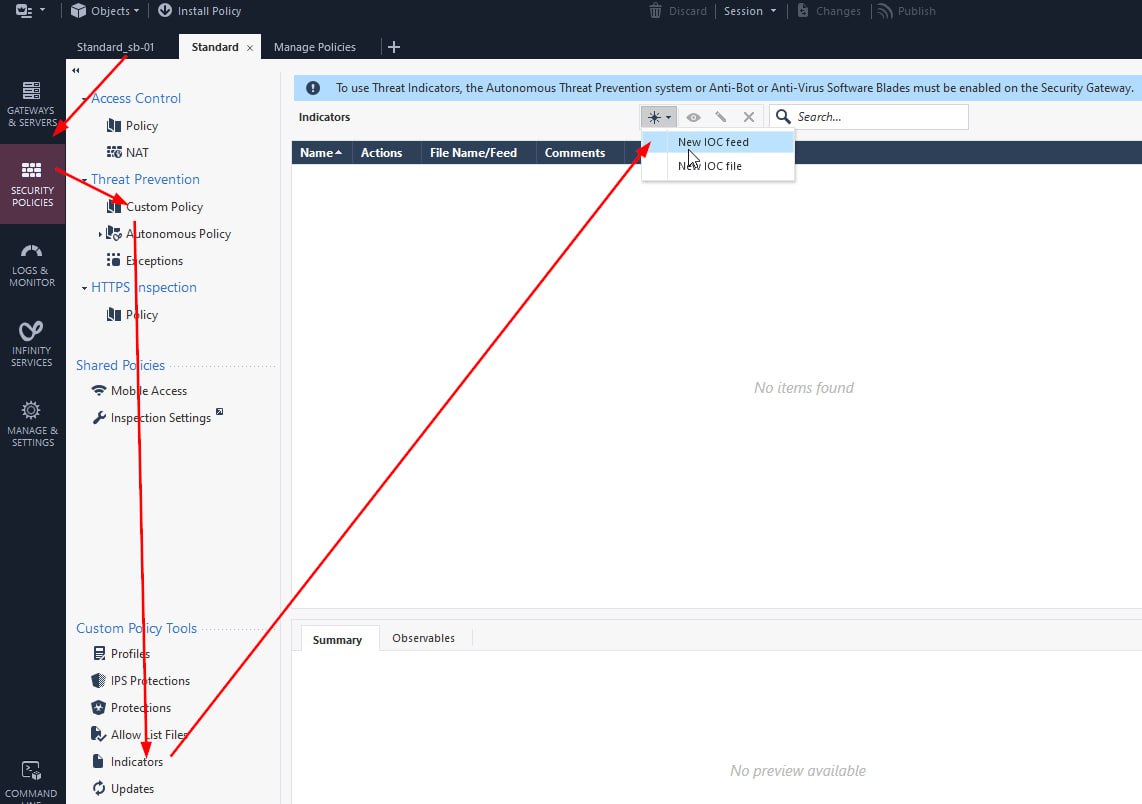
- The Indicator feed configuration window opens:
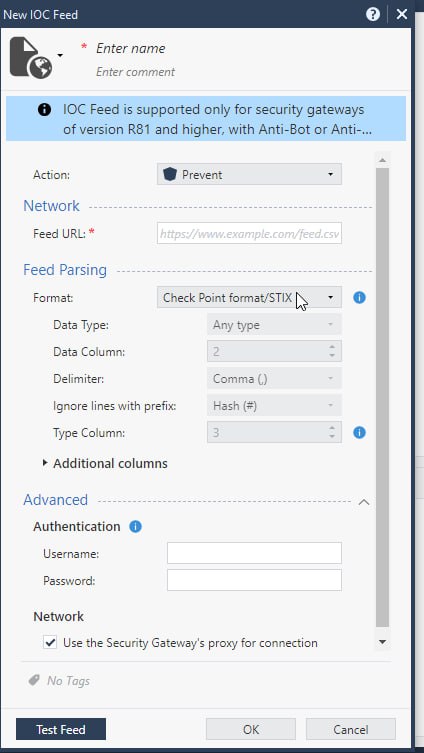
- Fill in the fields:
- For URL:
For all types of IoCs with high score (in this case it is 50 and higher):
https://api.rstcloud.net/v1/integrations/checkpoint/ip/50
https://api.rstcloud.net/v1/integrations/checkpoint/domain/50
https://api.rstcloud.net/v1/integrations/checkpoint/url/50
https://api.rstcloud.net/v1/integrations/checkpoint/hash/50
https://api.rstcloud.net/v1/integrations/checkpoint/ip_src/45
We recommend to use Score filter in the URL. For high-confidence and actual IOCs it is approximately 50-60 and higher scores, for informative ones it is score less than 30-40. In the middle is suspicious indicators. Each indicator has an individual score calculated based on its actuality and risk: what type of indicator it is, who is the reporter of the indicators, how many other people are already aware of that indicator, was that indicator exposed previously and many other contributing factors.
The higher the indicator score, the lower their false-positive rate. Pick the right threshold that will suit your environment.
For IoCs of specific categories (C2 servers, phishing, malware):
https://api.rstcloud.net/v1/integrations/checkpoint/ip/45/c2
https://api.rstcloud.net/v1/integrations/checkpoint/domain/45/phishing
https://api.rstcloud.net/v1/integrations/checkpoint/hash/45/malware
In general, the structure of request is:
https://api.rstcloud.net/v1/integrations/checkpoint/[ALLOWED_TYPES]/[ALLOWED_CATEGORIES]
Where:
ALLOWED_TYPES: "ip", "domain", "url", "hash", "ip_src"
ALLOWED_CATEGORIES: all, backdoor, badbot, banker, bootkit, botnet, c2, clicker, cryptomining, ddos, dns, downloader, drainer, dropper, fraud, generic, keylogger, malware, phishing, proxy, raas, ransomware, rat, rootkit, scam, scan, screenshotter, shellprobe, spam, spyware, stealer, tor_exit, trojan, vpn, vulndriver, webattack, wiper
Please contact us for your specific username and password.
The full guide on using Threat Intelligence with the Check Point NGFW:
Congratulations! You have successfully configured the RST Threat Feed in Check Point NGFW. You can now leverage the threat intelligence data in your security gateway.